The digital landscape is in a constant state of evolution, bringing forth both innovative solutions and complex security challenges. As networks grow more intricate and susceptible to vulnerabilities, the need for robust security measures has never been greater. One such measure that often goes overlooked is DHCP Option 82.
This article aims to equip you with the comprehensive knowledge and practical tools required to effectively implement DHCP Option 82. By doing so, you’ll fortify your network security, mitigate risks, and stay one step ahead in the ever-changing world of cybersecurity.
Jump to:
- What is DHCP Option 82?
- The Anatomy of Option 82
- Why Option 82 is Crucial for Security
- Implementing DHCP Option 82
- Troubleshooting and Common Pitfalls
- References
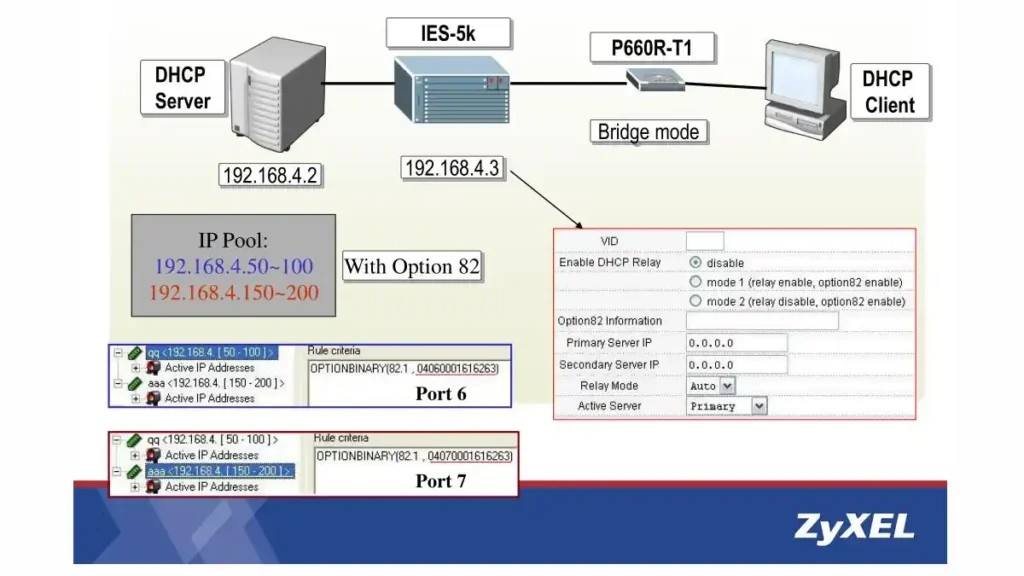
1. What is DHCP Option 82?
Brief Overview of DHCP
Before we delve into the intricacies of Option 82, it’s crucial to establish a fundamental understanding of DHCP, or Dynamic Host Configuration Protocol. In the simplest terms, DHCP is a network protocol used to dynamically assign IP addresses to devices in a network. This automates and centralizes the process, eliminating the need for manual IP address configuration.
Understanding DHCP Option 82
Now that we’ve skimmed the surface of DHCP, let’s dive deeply into the main subject of this article—Option 82. Known formally as the “DHCP Relay Agent Information Option,” this feature allows a DHCP relay agent to include additional information when forwarding client-originated DHCP packets to a DHCP server. Essentially, it serves as an additional layer of metadata, accompanying the basic DHCP information.
Components of Option 82
Option 82 comprises two primary sub-options:
- Circuit ID: This identifies the specific port and switch to which a device is connected.
- Remote ID: This is generally the MAC address of the relay agent or a user-defined string that helps in identifying the device.
This data is appended to DHCP packets, offering deeper insight into the network topology and the client’s point of attachment to the network.
Significance in Modern Networks
In contemporary network architectures, especially those employing VLANs and subnet masking, Option 82 is indispensable. It provides an additional set of eyes, so to speak, that helps in identifying the physical location of devices on the network. This is particularly useful in shared networks or public access environments like airports, hotels, and enterprise campuses.
How It Works
When a device requests an IP address, the DHCP relay agent inserts the Option 82 information into the DHCP packet. This packet then travels to the DHCP server, which takes this additional data into account before assigning an IP address. This allows the server to make more context-aware decisions, enhancing the security and efficiency of IP address allocation.
In summary, Option 82 serves as a linchpin in augmenting network security and efficiency. As we navigate through the following chapters, we will delve into why Option 82 is crucial for your network’s security and how you can seamlessly implement it into your existing infrastructure. Stay tuned.
2. The Anatomy of Option 82
As we delve deeper into the world of DHCP Option 82, it becomes increasingly evident that its true potential is encapsulated in its detailed anatomy. The sub-options and data fields it contains are not mere add-ons; they are vital components that provide a robust, context-rich layer of security and functionality. So, what exactly are these sub-options, and what roles do they play? Let’s dissect them one by one.
Key Sub-Options of Option 82
1. Circuit ID
The Circuit ID sub-option is a unique identifier for the network circuit to which a client is connected. This could be a particular Ethernet interface on a switch or a specific DSLAM port in a DSL network. The purpose is to provide a granular level of detail about the client’s exact location within the network architecture.
2. Remote ID
The Remote ID serves as another identifier but operates at a higher level, usually at the edge router or aggregation device. This ID can be manually configured to be the MAC address of the device or any other identifier deemed useful for tracking and security purposes.
Understanding Data Fields
Each of these sub-options contains specific data fields that provide additional context:
- Type: Specifies the sub-option type; Circuit ID or Remote ID.
- Length: Indicates the length of the data field that follows.
- Value: This is the actual data, be it a string, number, or MAC address, which gives the DHCP server the necessary context.
Use Cases: Where These Sub-Options Shine
The utilization of Circuit ID and Remote ID has far-reaching implications in various scenarios:
- Enterprise Networks: In large organizations with intricate networks, keeping track of where devices connect can be a herculean task. Option 82 can simplify this by providing exact location data for each device.
- Public WiFi Hotspots: In airports, hotels, and coffee shops, ensuring secure and efficient IP allocation is crucial. Option 82 allows for the segregation of users based on their point of connection.
- IoT Deployments: As IoT devices flood the market, their secure integration into existing networks becomes a significant concern. Option 82 offers an extra layer of security by identifying the exact point of connection for each device.
- Telecom Networks: In environments like DSL or Fiber-to-the-Home (FTTH), Option 82 can be invaluable in troubleshooting, as it allows network operators to pinpoint the exact location of any connectivity issues.
By understanding the anatomy of Option 82 and the richness of the data it can provide, network administrators are better equipped to implement smart, secure, and efficient network architectures. As we move to the next chapters, you’ll learn how to leverage these features for maximal security benefits. Stay tuned.
3. Why Option 82 is Crucial for Security
In today’s cybersecurity climate, where threats are not just probabilities but eventual certainties, every layer of security counts. While DHCP Option 82 might seem like a small cog in a vast machine, it plays a pivotal role in patching security loopholes and enhancing network integrity. Let’s explore how Option 82 acts as a linchpin in securing your network, highlighting its significance through real-world scenarios and its contributions to compliance and regulatory measures.
Closing Security Loopholes
Unauthorized Device Access
One of the most common security threats to networks is unauthorized device access. Without Option 82, any device can connect to a network port and receive an IP address, gaining potential access to network resources. The Circuit ID and Remote ID data fields serve as gatekeepers, providing a detailed log of which devices are connected to which ports, enabling swift identification and neutralization of unauthorized devices.
IP Spoofing
IP spoofing involves a device disguising its IP address to imitate another device. Option 82 adds an extra layer of verification by associating IP addresses with specific ports and remote IDs. This makes it more challenging for attackers to successfully spoof an IP address, as they would also need to manipulate the Option 82 data, which is far more complex and challenging.
Real-world Scenarios
Corporate Espionage
Imagine an individual managing to plug a device into an unsecured port in a corporate office. Without Option 82, this unauthorized device could potentially gain access to sensitive information. With Option 82 enabled, the network administrators would instantly recognize the new, unapproved device, allowing for immediate action.
Public Internet Access Points
In locations like airports or hotels, the public nature of the network makes it ripe for exploitation. An attacker might connect a malicious device to the network to steal data from other users. Option 82 allows for quick identification and isolation of such devices, providing a more secure browsing experience for legitimate users.
Compliance and Regulatory Measures
Several cybersecurity standards, like PCI DSS for payment card security, require stringent measures for tracking and managing devices on a network. The detailed logging enabled by DHCP Option 82 can be invaluable in audits, ensuring that you meet or exceed these regulatory requirements. It’s not just about following the rules; it’s about exceeding them to ensure maximal network integrity.
In summary, the relevance of DHCP Option 82 extends far beyond mere IP allocation. It acts as an essential tool in your cybersecurity arsenal, providing an additional layer of defense against unauthorized access and potential malicious activities. As we move on to the implementation stage in the next chapter, you’ll see just how straightforward it is to add this robust security feature to your network. Stay tuned.
4. Implementing DHCP Option 82
You’ve read about the whys and the hows, the nitty-gritty details, and the security imperatives. Now, it’s time for action. Implementing DHCP Option 82 might seem like a daunting task, but with the right guidelines, it can be as seamless as setting up a standard DHCP server. Let’s dive into a step-by-step guide on how to implement this critical security feature, discussing the prerequisites and best practices along the way.
Prerequisites
Before embarking on the implementation journey, ensure you have the following in place:
- Network Hardware: Make sure your routers and switches support DHCP Option 82.
- Software: Ensure your DHCP server software is updated and supports Option 82 functionality.
- Knowledge: Familiarize yourself with your network architecture and DHCP configuration settings.
- Backup: Always take a backup of your current configuration settings before making changes.
Step-By-Step Guide
Step 1: Preliminary Assessment
Conduct a thorough assessment of your network to identify the crucial points where Option 82 needs to be enabled—such as routers, switches, or other relay agents.
Step 2: Update and Configure the DHCP Server
Ensure that your DHCP server is capable of interpreting Option 82. Update your server’s DHCP configuration to enable Option 82 support.
Step 3: Configure Network Devices
On each network device (router, switch, etc.), enable the insertion of Option 82 information. This typically involves navigating to the DHCP settings and enabling the appropriate features.
Step 4: Define Circuit ID and Remote ID
On each relay agent, configure the Circuit ID and Remote ID values as required by your organization’s security policy.
Step 5: Testing
Once everything is set up, test the system to make sure Option 82 information is correctly appended to the DHCP requests. Monitor the logs to validate successful implementation.
Step 6: Roll Out
After successful testing, roll out the implementation across your network. Keep a close eye on logs and any security alerts to ensure everything is working as expected.
Best Practices for Smooth Implementation
- Documentation: Keep a detailed record of every configuration change, making it easier to backtrack if issues arise.
- Segmentation: Roll out the changes in phases, starting with non-critical areas of your network.
- Monitoring: Continuously monitor DHCP logs for any anomalies, especially during the initial implementation phase.
- Training: Make sure the team responsible for network management understands the implications and usage of Option 82.
- Regular Updates: Keep all your devices and server software up-to-date to ensure continued compatibility and security.
By following these steps and best practices, you’ll not only implement DHCP Option 82 successfully but also significantly bolster your network’s security posture. As you proceed, remember that the aim is not just to meet security standards but to create an impermeable network environment. In the next chapter, we’ll cover troubleshooting and how to avoid common pitfalls, sealing your mastery over DHCP Option 82. Stay tuned.
5. Troubleshooting and Common Pitfalls
Congratulations, you’ve successfully implemented DHCP Option 82—or so you thought until you noticed something awry. As with any technology, things may not go as smoothly as planned. It’s crucial to be prepared for any hiccups that may occur during or after the implementation process. This chapter is your guide to navigating the common pitfalls, offering troubleshooting tips to set you back on the right path.
Common Issues and Troubleshooting Tips
1. Inconsistent Option 82 Information
- Symptom: The DHCP server is not assigning addresses correctly, or you notice inconsistencies in Option 82 information across devices.
- Solution: Double-check your DHCP server and relay agent configurations to ensure they match. Re-sync any devices that may have outdated or incorrect settings.
2. Poorly Defined Circuit IDs and Remote IDs
- Symptom: You find that the IDs do not accurately reflect the network topology or aren’t useful for tracking devices.
- Solution: Reevaluate your Circuit ID and Remote ID definitions. Ensure they are logically structured and relevant for your security needs.
3. Missing Logs or Incomplete Data
- Symptom: Logs are either missing or do not contain the expected Option 82 data.
- Solution: Ensure your logging settings capture the required information. Double-check your log paths and storage settings to ensure data is being recorded and stored correctly.
4. Device Compatibility Issues
- Symptom: Older devices on the network are not supporting Option 82 features.
- Solution: Update firmware if possible. For devices that can’t be updated, consider network segmentation to maintain a secure environment.
Potential Pitfalls and How to Avoid Them
1. Insufficient Testing
- Pitfall: Rolling out the implementation network-wide without thorough testing.
- Avoidance: Always test on a smaller, controlled environment first. Monitor for anomalies before a full-scale rollout.
2. Neglecting Backups
- Pitfall: Not backing up your current configurations before making changes.
- Avoidance: Always maintain up-to-date backups. This is a lifeline you cannot afford to cut.
3. Inadequate Monitoring
- Pitfall: Failing to continuously monitor the network post-implementation.
- Avoidance: Implement real-time monitoring and alerting systems to catch any issues as soon as they arise.
4. Lack of Documentation
- Pitfall: Poorly documented changes and configurations.
- Avoidance: Keep detailed records of each change, its purpose, and its effect. Good documentation is invaluable for future troubleshooting and audits.
By preparing for these common issues and potential pitfalls, you’re adding another layer of assurance to your Option 82 implementation. This foresight will serve you well, not just in maintaining a secure network but also in fostering an environment of best practices within your organization. Implementing DHCP Option 82 is a commendable step towards a more secure network. Now that you are equipped with the tools and knowledge to both implement and troubleshoot this feature, you’re well on your way to a fortified network. Thank you for sticking around, and stay secure.