Welcome to a comprehensive journey through the realm of zero-day vulnerabilities—a subject that intrigues cybersecurity experts and haunts IT administrators. What are zero-day vulnerabilities, and why are they so significant in the landscape of cybersecurity?
In this article, we dissect the life cycle of a zero-day, from its initial discovery to its eventual patching. We’ll explore the various methods attackers use to exploit these vulnerabilities and the measures you can take to mitigate their impact. If you’re interested in understanding the depth of zero-days, including real-world examples, this article is your authoritative guide. Buckle up as we unravel the complexities and nuances of zero-day vulnerabilities.
In this article:
- What is a Zero-Day Vulnerability?
- How Are Zero-Days Discovered?
- Exploitation of Zero-Days: Methods and Motives
- Patching and Response: How Vendors and Security Teams React
- Risk Management: Steps to Mitigate the Impact
- Case Studies: Famous Zero-Day Attacks
- Conclusion
- References
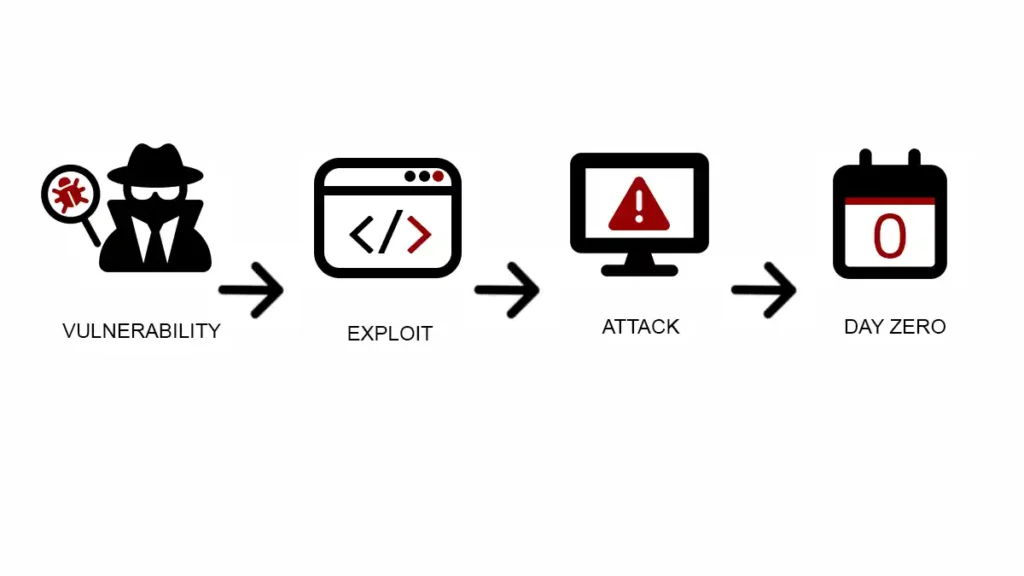
1. What is a Zero-Day Vulnerability?
The term “zero-day” refers to the number of days a vendor has had to address a discovered vulnerability. In essence, a zero-day vulnerability is a software or hardware flaw unknown to the vendor but known to a third party, most likely a hacker or cybersecurity researcher. Because the vendor is unaware of the vulnerability, no official patches or solutions exist, rendering it a lucrative target for cybercriminals.
Technical Aspects of a Zero-Day Vulnerability
Zero-day vulnerabilities occur in the source code of a software application or in the firmware of hardware devices. These are often complex and not straightforward to detect. A zero-day could manifest as a buffer overflow, race condition, or even a simple logic error in the software code. Regardless of the type, the underlying theme is the same: it is an unaddressed flaw that can potentially be exploited.
Here are some key attributes of zero-day vulnerabilities:
- Exploit Vector: The path or method through which the vulnerability is activated or exploited. This could be a particular function in a software application or a specific hardware interaction.
- Payload: This is the outcome of exploiting the vulnerability. For instance, it could be unauthorized access, data theft, or the execution of arbitrary code.
- Attack Surface: This represents all the different points where an attacker could exploit the vulnerability. A broad attack surface generally increases the risk associated with a zero-day.
- Severity: Not all zero-days are created equal. Severity ratings are used to identify how critical a particular zero-day might be, factoring in aspects such as the potential for data loss, system compromise, and the ease of exploitation.
Static vs. Dynamic Analysis
Identifying zero-days often involves a combination of static and dynamic code analysis.
- Static Analysis: This entails reviewing the software code without executing the program, looking for potential vulnerabilities purely from a code-perspective.
- Dynamic Analysis: In this method, the software is run in a controlled environment to analyze its behavior and pinpoint any abnormal actions that could indicate a vulnerability.
Why Zero-Days Are Different
What sets a zero-day apart from other vulnerabilities is the timeframe in which it exists. Specifically, a zero-day vulnerability has:
- No Vendor Patch: Since the vendor is unaware, there is no official fix.
- Limited Mitigation: The absence of a patch means that mitigation relies on third-party solutions or temporary workarounds.
- High Value: Zero-days are highly valuable, especially in the world of cybercrime and state-sponsored attacks. They can be sold on the dark web or used for significant strategic advantage.
The Life Cycle of a Zero-Day
Understanding a zero-day involves grasping its life cycle, which typically follows these stages:
- Discovery: The vulnerability is found either by a researcher, a user, or a malicious actor.
- Exploitation: The vulnerability is exploited, often clandestinely.
- Detection: The exploitation is detected, either by the vendor or the community.
- Analysis: The vulnerability is analyzed for scope and impact.
- Patch Development: A fix is created by the vendor.
- Patch Deployment: The fix is distributed to users.
In conclusion, a zero-day vulnerability is a chink in the armor of software or hardware that is not yet known to the vendor but may be known and exploited by attackers. Its unknown status and the absence of a ready solution make it particularly dangerous and prized in the realm of cybersecurity.
2. How Are Zero-Days Discovered?
The discovery of zero-day vulnerabilities is a complex process that involves various actors, from security researchers and ethical hackers to cybercriminals and intelligence agencies. Different parties may use contrasting methods and have diverging motivations, but the end result is the same: the unearthing of an unpatched security flaw. In this chapter, we will delve into the primary techniques and practices used to identify zero-days.
Bug Bounty Programs
Many software companies run bug bounty programs that incentivize ethical hackers and security researchers to find vulnerabilities and responsibly disclose them. Participants in these programs often employ rigorous testing methods, including fuzzing and reverse engineering, to identify zero-day vulnerabilities.
Source Code Analysis
- Static Analysis: This involves a thorough examination of a software’s source code. Researchers look for code smells, potential buffer overflows, and any other markers that may indicate a vulnerability.
- Dynamic Analysis: Unlike static analysis, dynamic analysis involves running the software and examining its behavior to identify abnormalities that might indicate a vulnerability.
Fuzzing
Fuzzing is an automated testing technique that involves feeding random or malformed data into a software application to check how it reacts. This technique is particularly useful for identifying vulnerabilities that are not apparent through regular code analysis.
Reverse Engineering
Highly skilled researchers may choose to disassemble and reverse engineer a compiled application. This is a time-consuming process but often reveals vulnerabilities that are deeply buried within the code and would otherwise go unnoticed.
Threat Intelligence
Some zero-day vulnerabilities are discovered through active monitoring of underground forums, chat groups, and other spaces where cybercriminals congregate. Threat intelligence professionals mine these spaces for information, and occasionally, zero-days are discovered and disclosed before they can be exploited maliciously.
Nation-State Activity
Intelligence agencies around the world actively look for zero-day vulnerabilities, not only for defense but for offensive capabilities as well. While these discoveries are often classified, they can sometimes surface if an agency decides to disclose the vulnerability for broader security reasons.
Accidental Discovery
Not all zero-day vulnerabilities are found intentionally. End-users, system administrators, or developers may stumble upon a vulnerability while troubleshooting software issues or performing routine maintenance tasks.
Post-Exploit Analysis
In some instances, zero-day vulnerabilities are discovered only after they have been exploited. Security analysts may reverse-engineer malware that successfully infiltrated a system to identify the zero-day it exploited, thereby initiating the process to patch it.
The discovery of zero-day vulnerabilities is a multifaceted process involving a variety of methods and actors. While some techniques, such as fuzzing and code analysis, are proactive, others like post-exploit analysis are reactive. Regardless of the method or the entity behind the discovery, what’s crucial is that these vulnerabilities are identified, studied, and ultimately patched to enhance cybersecurity.
3. Exploitation of Zero-Days: Methods and Motives
While the discovery of zero-day vulnerabilities is a topic of interest for security researchers, ethical hackers, and software vendors, understanding how these vulnerabilities are exploited is equally crucial. Exploitation varies depending on the motives behind the attack, the resources available, and the methods used. This chapter will provide an in-depth look at the tactics, techniques, and procedures (TTPs) associated with exploiting zero-day vulnerabilities.
Methods of Exploitation
Drive-by Downloads
A common vector for exploiting browser-based zero-days, drive-by downloads occur when a user visits a malicious or compromised website, leading to the automatic download of malware exploiting a zero-day.
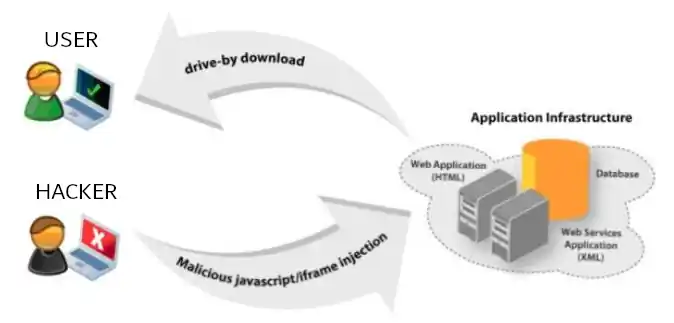
Spear Phishing
In targeted attacks like spear phishing, attackers often send emails with attachments that exploit zero-day vulnerabilities in document readers, spreadsheets, or other application software. See: Phishing.
Malvertising
Using online advertisements as a medium, attackers inject malicious code that exploits zero-days in web browsers or plugins. Unsuspecting users who click on these ads inadvertently initiate the exploit.
Watering Hole Attacks
In this method, attackers compromise websites frequently visited by their target group. By injecting malicious code into these websites, they exploit zero-day vulnerabilities in the browsers of the targeted audience.
Malware Bundling
Cybercriminals may bundle malware exploiting zero-day vulnerabilities with legitimate software, essentially Trojanizing the application to facilitate the attack.
Motives Behind Exploitation
Financial Gain
Many attackers aim to steal financial information, such as credit card numbers or banking credentials, which they can sell on the dark web or use for unauthorized transactions.
Espionage
Government and intelligence agencies, as well as corporate spies, may exploit zero-days to gain unauthorized access to sensitive information, ranging from classified military secrets to intellectual property.
Competitive Advantage
In the business landscape, companies may exploit zero-days to spy on competitors, thereby gaining an unfair advantage in the marketplace.
Activism and ‘Hacktivism’
Some exploit zero-day vulnerabilities to further political, environmental, or social objectives. They target organizations they perceive as harmful to their cause.
Research and Reconnaissance
Certain cyber actors exploit zero-days for research purposes or to gather information for future attacks. These activities usually form part of a broader, more sophisticated campaign.
Tools Used for Exploitation
Attackers use a variety of tools and frameworks for exploiting zero-day vulnerabilities, including:
- Metasploit: A penetration testing framework that has modules for exploiting known and unknown vulnerabilities.
- BeEF (Browser Exploitation Framework): Targeted towards web browsers, this tool is designed for exploiting browser-based zero-days.
- Exploit Kits: These are pre-packaged sets of code and attacks that are designed to exploit multiple vulnerabilities, including zero-days.
- Custom Tools: Advanced Persistent Threat (APT) groups often develop proprietary tools tailored to exploit specific zero-day vulnerabilities.
Mitigation and Defense
While not the primary focus of this chapter, it’s worth noting that intrusion detection systems (IDS), endpoint protection platforms, and robust patch management strategies can mitigate the risk of zero-day exploits.
Understanding the exploitation of zero-day vulnerabilities requires a multi-faceted view that includes the methods used, the motives behind these actions, and the tools that facilitate such attacks. By having a comprehensive grasp of these elements, cybersecurity professionals can better prepare for, and defend against, these unpredictable and often devastating attacks.
4. Patching and Response: How Vendors and Security Teams React
The discovery of a zero-day vulnerability is only the first part of a long and complex journey towards ensuring network and data security. Once a zero-day is discovered, it sets off a race against time for software vendors and security teams. Their goal? To understand the vulnerability, develop a patch, and distribute it before attackers can take advantage. This chapter delves into the various stages of how vendors and security teams react when a zero-day vulnerability comes to light.
Initial Discovery and Verification
Vendor Notification
Upon discovering a zero-day, responsible security researchers typically notify the software vendor privately to avoid public exploitation. This is known as “responsible disclosure.”
Vulnerability Assessment
Vendors or third-party security researchers validate the vulnerability to confirm its existence and evaluate its severity. This is usually quantified using scores such as CVSS (Common Vulnerability Scoring System).
Patch Development
Internal Analysis
Software vendors assemble specialized teams of engineers to analyze the vulnerability in-depth. This involves understanding its mechanics, identifying affected code bases, and assessing its impact.
Patch Creation
The technical team then develops a software patch or update to fix the vulnerability. This involves modifying the code to eliminate the security flaw without affecting the software’s functionality.
Testing and Quality Assurance
Before releasing the patch, it undergoes a series of rigorous tests to ensure it successfully mitigates the vulnerability without introducing new issues. This phase may involve:
- Unit Testing
- Integration Testing
- Performance Testing
- Security Testing
Patch Distribution
Public Disclosure
Once a patch is ready, vendors usually make a public announcement about the vulnerability, often coordinating with the original security researchers for simultaneous disclosure.
Automatic Updates
For consumer software and cloud services, patches are generally pushed automatically to users. This helps in quick mitigation but might not be applicable for enterprise environments with specific compliance requirements. See: Windows Updates.
Manual Downloads
For enterprise systems and critical infrastructure, patches are often made available for manual download and implementation, allowing IT teams to test them in their specific environments before widespread deployment.
Incident Response Teams
Security teams play a crucial role throughout this process:
- Monitoring for Exploitation: They keep an eye on network traffic and system behavior to detect any signs of active exploitation.
- Communication: They coordinate with vendors and share information within industry-specific Information Sharing and Analysis Centers (ISACs).
- Internal Patching: After assessing the patch’s compatibility and stability, they roll it out across the organization.
The lifecycle of patching a zero-day vulnerability is a complex, multi-stage process requiring coordination between vendors, security researchers, and in-house security teams. Timely and effective response can mean the difference between a minor security incident and a major data breach. Understanding this process can prepare organizations to act swiftly and efficiently, mitigating risks and safeguarding assets.
5. Risk Management: Steps to Mitigate the Impact
Managing the risk associated with zero-day vulnerabilities is a critical aspect of cybersecurity. The unpredictable nature of these vulnerabilities makes them exceptionally challenging to address. While vendors and security teams work to create and distribute patches, organizations must take immediate actions to reduce exposure and safeguard assets. This chapter explores comprehensive steps for risk management to mitigate the impact of zero-day vulnerabilities.
Initial Risk Assessment
Identify Affected Systems
The first step is to determine which systems, applications, or services are vulnerable. Inventory management tools can be invaluable in this process.
Severity Analysis
Perform a risk assessment based on factors such as the sensitivity of the data involved, the criticality of the affected systems, and the vulnerability’s potential impact.
Short-Term Mitigations
Network Segmentation
Isolate affected systems from the network to prevent lateral movements by potential attackers. (learn more)
Use of Web Application Firewalls (WAF)
Deploy WAFs with custom rules designed to detect and block attempts to exploit the zero-day vulnerability.
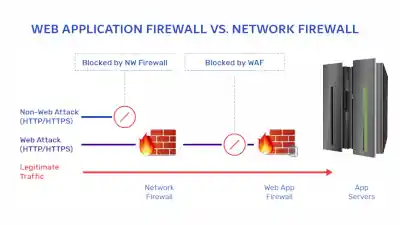
Traffic Monitoring
Enhance monitoring to identify unusual patterns or activities that could indicate exploitation of the vulnerability.
Disable Affected Features or Services
If the vulnerability is tied to a specific feature or service, consider temporarily disabling it until a patch becomes available.
Long-Term Mitigations
Patch Management Strategy
Develop a robust patch management strategy to ensure the speedy implementation of fixes once they are released.
User Training and Awareness
Educate employees about the risks associated with zero-day vulnerabilities and best practices for avoiding potential exploitation techniques like phishing.
Incident Response Plan
Create or update an incident response plan tailored to deal with zero-day vulnerabilities, including specific roles and communication protocols.
Vendor Collaboration
Subscribe to Vendor Updates
Stay up-to-date with security advisories from software vendors and cyber threat intelligence services.
Beta Testing
Consider participating in vendor-sponsored beta testing of patches for early access and to contribute to the development process.
Continuous Monitoring and Updating
Log Reviews
Regularly review system and security logs for any indications of unusual or unauthorized activities.
Threat Hunting
Proactively search for indicators of compromise within your network, even after patches are applied.
Update Risk Assessment
Constantly revise risk assessments based on new threat intelligence and system changes.
Risk management for zero-day vulnerabilities is a dynamic, multi-faceted endeavor that demands continuous vigilance. Through immediate short-term actions and ongoing long-term strategies, organizations can minimize the impact and improve resilience against these unpredictable threats. Importantly, risk management should be an organization-wide responsibility, incorporating technologies, processes, and people to form a cohesive defense against zero-day vulnerabilities.
6. Case Studies: Famous Zero-Day Attacks
The world of cybersecurity is filled with dramatic tales where the invisible hand of a hacker wreaks havoc by exploiting zero-day vulnerabilities. These real-life stories serve as cautionary tales, highlighting the urgent need for robust cybersecurity measures. In this captivating chapter, we delve into some of the most famous zero-day attacks that shook the digital world.
1: Stuxnet: The Digital Weapon
Overview
Stuxnet is often considered the first cyberweapon. Discovered in 2010, this worm targeted Siemens industrial control systems with the aim of sabotaging Iran’s nuclear program.
How It Worked
The worm exploited four zero-day vulnerabilities in Microsoft Windows and spread through USB drives. Once inside a network, it searched for specific Siemens software and altered the speed of centrifuges, causing physical damage.
Impact and Lessons
Stuxnet demonstrated that cyberattacks could have real-world consequences, affecting national security. It changed the landscape of cybersecurity, showing that state-sponsored attacks could be a new form of warfare.
2: Heartbleed: The Bug that Exposed the Internet
Overview
In 2014, the Heartbleed bug was discovered in OpenSSL, a widely used open-source cryptographic library. It exposed sensitive data, including user passwords and encryption keys, across the internet.
How It Worked
Heartbleed exploited a vulnerability in the SSL/TLS protocol to trick servers into leaking data stored in their memory.
Impact and Lessons
Millions of websites were affected, and users were advised to change their passwords. The incident raised questions about the security of open-source software and the responsibility for maintaining such widely used systems.
3: Equifax: The Breach that Cost Billions
Overview
In 2017, a data breach at Equifax, one of the largest credit reporting agencies, exposed the personal data of 147 million Americans.
How It Worked
Hackers exploited a zero-day vulnerability in Apache Struts, a tool for building web applications. Despite a patch being available, Equifax failed to update its systems in time.
Impact and Lessons
The breach led to a congressional investigation, and Equifax faced billions in fines and settlements. It was a wake-up call for enterprises to prioritize patch management.
4: EternalBlue: A Stolen NSA Tool Unleashed
Overview
In 2017, the WannaCry ransomware attack infected over 200,000 computers across 150 countries.
How It Worked
WannaCry leveraged EternalBlue, an exploit developed by the NSA and leaked by a hacking group. The exploit took advantage of a zero-day vulnerability in Windows’ Server Message Block protocol.
Impact and Lessons
The attack paralyzed hospitals, banks, and other institutions and served as a grim reminder of the dangers when cyberweapons fall into the wrong hands.
Certainly, zero-day attacks such as these act as sobering wake-up calls, revealing that no system can ever be fully secure. Indeed, they highlight the ongoing cat-and-mouse battle between cybersecurity experts and malicious hackers. With each harrowing incident, we glean hard-earned lessons that enrich our collective wisdom on safeguarding the digital realm. For instance, whether it’s the diligent patching of software, careful vetting of open-source tools, or a thoughtful reevaluation of the ethical dimensions of cyber weaponry, these infamous attacks undeniably influence how we tackle cybersecurity today.
7. Conclusion
Certainly, zero-day vulnerabilities and the ensuing attacks cast a haunting shadow over our digital existence. These hidden flaws not only unveil the shortcomings of our present cybersecurity strategies, but they also compel us to anticipate and prepare for unknown threats looming on the horizon.
Transitioning from theory to real-world examples, we’ve delved into numerous case studies that highlight the far-reaching consequences of exploited vulnerabilities. These range from jeopardizing national security to triggering large-scale data breaches that impact millions of lives. Therefore, staying vigilant about these risks and proactively updating our security protocols emerge as vital steps in fortifying our digital defenses. Ultimately, this in-depth exploration into the realm of zero-day vulnerabilities equips you with the essential knowledge to confidently navigate this ever-shifting cyber landscape.
8. References
- Chen, T. M., Abu-Nimeh, S. (2011). “Lessons from Stuxnet.” Computer, 44(4), 91-93.
- Durumeric, Z., Kasten, J., Adrian, D., et al. (2014). “The Matter of Heartbleed.” In Proceedings of the 2014 Conference on Internet Measurement Conference, 475-488.
- U.S. House of Representatives, Committee on Oversight and Government Reform. (2018). “The Equifax Data Breach.”
- Allodi, L., Massacci, F. (2017). “Security Events and Vulnerability Data for Cybersecurity Risk Estimation.” Risk Analysis, 37(8), 1606-1627.
- BBC News. (2017). “WannaCry ransomware cyber-attacks slow but fears remain.” Retrieved from https://www.bbc.com/news/technology-39915440
- National Cyber Security Centre. (2017). “WannaCry Ransomware Guidance.”
- NSA-CSS. (2017). “Advisory on ‘EternalBlue’ Exploit.”