Account lockout is a security measure employed in computing environments to protect user accounts against unauthorized access attempts. Essentially, it is a process that temporarily or permanently disables a user account after a series of failed login attempts. This mechanism is crucial in mitigating the risk of brute-force attacks, where an attacker attempts to gain access by systematically trying numerous password combinations.
In this comprehensive guide, we will explore the nuances of account lockout policies, their implementation, challenges, and best practices.
Table of Contents:
- Understanding Account Lockout Policies
- Implementing Account Lockout in Different Systems
- Account Lockout in Windows 10/11 and Windows Server 2019
- Challenges and Considerations
- Best Practices for Account Lockout Policies
- Advanced Account Lockout Techniques
- Conclusion
1. Understanding Account Lockout Policies
Account lockout policies are a set of rules that define when and how an account should be locked out. These policies typically specify the number of failed login attempts that trigger a lockout and the duration of the lockout period. For example, a policy might lock an account for 30 minutes after three failed login attempts.
- Threshold for Failed Attempts: This defines the number of incorrect password submissions after which an account is locked.
- Lockout Duration: The period during which the account remains inaccessible after reaching the threshold.
- Reset Counter: This policy determines the time frame after which the count of failed attempts is reset.
TIP
Use account lockout only for high-security networks. In a low-security environment, users can become frustrated if they lock themselves out by mistyping their password, and administrators must cope with the additional overhead and bother of unlocking these accounts.
2. Implementing Account Lockout in Different Systems
The implementation of account lockout varies across different platforms and systems.
- Windows Active Directory: In Active Directory environments, account lockout policies can be configured using Group Policy Objects (GPOs).
- UNIX/Linux Systems: These often use Pluggable Authentication Modules (PAM) to implement account lockout mechanisms.
- Cloud Services: Cloud-based platforms like AWS and Azure provide their mechanisms for setting account lockout policies.
3. Account Lockout in Windows 10/11 and Windows Server 2019
Understanding Account Lockout in Windows Environments
Account lockout in Windows 10/11 and Windows Server 2019 is a critical security feature designed to prevent unauthorized access to user accounts. It is particularly vital in environments where sensitive data is accessed or in scenarios where the security of user accounts is paramount. This chapter delves into how account lockout works in these Windows systems, focusing on its configuration, behavior, and implications.
Configuration of Account Lockout Policies
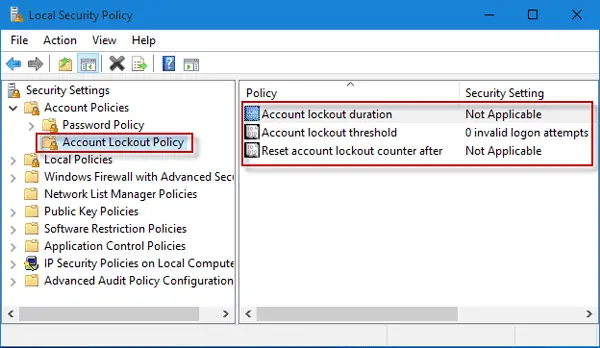
- Accessing Account Lockout Policies: Account lockout policies in Windows 10/11 and Windows Server 2019 are configured through the Local Security Policy or via Group Policy in a domain environment. Administrators can access these settings by navigating to the
Security Settings -> Account Policies -> Account Lockout Policyin the Group Policy Editor. - Key Settings:
- Account Lockout Threshold: Determines the number of failed login attempts that will trigger an account lockout. Setting this value to ‘0’ effectively disables the account lockout feature.
- Account Lockout Duration: Specifies the length of time a user must wait after being locked out of their account. This can range from a few minutes to indefinite periods, requiring manual reset by an administrator.
- Reset Account Lockout Counter After: Defines the time frame after which the count of failed login attempts is reset to zero.
Behavior of Account Lockout in Practice
When a user exceeds the specified number of failed login attempts (as defined in the Account Lockout Threshold), Windows locks the account for the duration specified in the Account Lockout Duration setting. During this period, even if the correct credentials are entered, the system will not allow access to the locked account.
Implications and Best Practices
- Security vs. Usability: While strict account lockout policies enhance security by thwarting brute-force attacks, they can also lead to increased support calls and user frustration due to accidental lockouts. Striking a balance is key.
- Audit Policies: Administrators should enable audit policies to log account lockout events. This aids in identifying potential security incidents or assessing the impact of the account lockout settings.
- Considerations for Service Accounts: Special attention should be given to service accounts in Windows Server environments. Frequent lockouts of service accounts can lead to significant disruptions in services and applications.
Additional Considerations for Windows Server 2019
In Windows Server 2019, account lockout policies can also be managed using PowerShell, providing a more streamlined and automated approach, especially useful in large-scale or complex domain environments.
4. Challenges and Considerations
While account lockouts are essential for security, they come with their challenges.
- User Inconvenience: Frequent lockouts can frustrate legitimate users, especially in high-security settings with strict policies.
- Denial of Service (DoS) Risks: Attackers might intentionally trigger lockouts to lock legitimate users out of their accounts, leading to a potential denial of service.
- Balancing Security and Usability: Finding the right balance between security (preventing unauthorized access) and usability (ensuring legitimate users have access) is crucial.
5. Best Practices for Account Lockout Policies
- Reasonable Thresholds: Set a threshold for failed attempts that is high enough to allow for user error but low enough to deter attackers.
- Progressive Lockouts: Implementing progressive lockouts, where subsequent lockouts have increasing durations, can be effective.
- User Education: Educate users about password security to reduce the number of lockout incidents due to forgotten passwords.
- Monitoring and Alerts: Implement monitoring systems to alert administrators of unusual lockout activities, which could indicate a potential attack.
6. Advanced Account Lockout Techniques
- Risk-Based Authentication: Implementing additional security checks for suspicious login attempts before locking out the account.
- CAPTCHA Integration: Use CAPTCHA challenges after a few failed attempts to differentiate between human users and automated attack scripts.
- Machine Learning: Employing machine learning algorithms to detect and respond to unusual login patterns.
7. Conclusion
Account lockout is a fundamental aspect of modern cybersecurity strategies. While effective in preventing brute-force attacks, it is essential to implement these policies judiciously to balance security with user convenience.
By understanding the various aspects of account lockout policies and following best practices, organizations can significantly enhance their security posture while maintaining a user-friendly environment.