In the intricate landscape of Windows environments, network security auditing emerges as a pivotal aspect of safeguarding information and ensuring system integrity.
This article dives into the core of network security auditing within Windows settings, unraveling its significance, methodologies, and best practices. We will explore how to configure and interpret Windows audit policies, utilize essential tools like Event Viewer, and integrate advanced auditing solutions. By equipping readers with practical knowledge and actionable strategies, this piece aims to enhance the security posture of Windows networks, addressing the challenges faced by IT professionals in today’s dynamic cyber environment.
Table of Contents:
- Introduction to Network Security Auditing in Windows
- Setting Up Windows Audit Policies
- Understanding Windows Security Logs
- Using Windows Event Viewer for Auditing
- Advanced Tools and Techniques for Windows Auditing
- Best Practices in Windows Security Auditing
- Case Studies: Real-World Applications
- Conclusion
- References

1. Introduction to Network Security Auditing in Windows
Network security auditing in Windows environments is an indispensable practice for identifying vulnerabilities, ensuring compliance, and maintaining robust security. This process involves examining and reviewing the security measures in place to protect data, applications, and the network infrastructure within Windows systems.
The cornerstone of effective network security auditing in Windows is a thorough understanding of the operating system’s security features and how they can be leveraged to detect and prevent unauthorized access or malicious activities. This includes scrutinizing user access rights, system updates, network connections, and application security.
Windows network security auditing also plays a crucial role in compliance. With various regulations mandating stringent data protection standards, auditing helps ensure that Windows environments meet these requirements, avoiding potential legal and financial repercussions.
In this chapter, we explore the fundamentals of network security auditing in Windows, setting the stage for a deep dive into specific tools, techniques, and best practices in subsequent chapters.
2. Setting Up Windows Audit Policies
Setting up audit policies in Windows is a critical step in monitoring and securing your network. Focusing on recent Microsoft operating systems, such as Windows Server 2019 and Windows 10, here’s how to effectively configure audit policies:
- Accessing Audit Policy Configuration:
- Open the Group Policy Management Console (GPMC).
- Navigate to
Computer Configuration→Windows Settings→Security Settings→Advanced Audit Policy Configuration.
- Configuring Audit Categories:
- Windows provides a range of audit categories, such as Account Logon, Account Management, Detailed Tracking, and Object Access.
- Define policies for each category based on your security requirements.
- Audit Policy Recommendations:
- For a secure environment, enable auditing for successful and failed logon attempts, privilege use, directory service access, and object access attempts.
- Tailor policies to your specific network environment and compliance needs.
- Implementing Advanced Auditing:
- Utilize Advanced Audit Policy Configuration for more granular control over auditing.
- Set policies for specific events like Kerberos authentication service and network policy server.
- Testing and Verification:
- After setting up policies, test them to ensure they’re capturing the desired information.
- Use Event Viewer to review the audit logs and adjust policies as needed.
Properly setting up Windows audit policies is a foundational step in network security auditing, providing visibility into activities within your network and alerting you to potential security issues.
3. Understanding Windows Security Logs
Windows Security Logs are a vital component in the auditing process, serving as a detailed record of security-related events within a Windows environment.
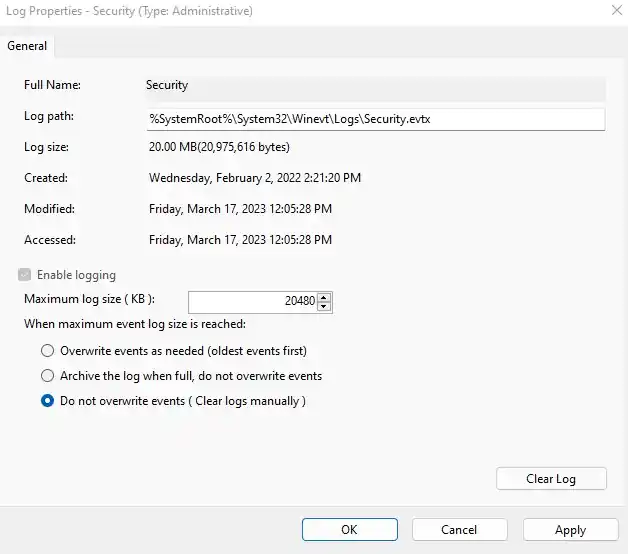
These logs are essential for identifying suspicious activities, investigating security incidents, and ensuring compliance with security policies.
- Types of Events Tracked:
- Security logs track various events, including user logons/logoffs, system startup/shutdown, file and object access, policy changes, and account management activities.
- Log Management:
- Regularly monitor and archive logs to prevent them from being overwritten. This is crucial for maintaining a historical record of events.
- Implement log management tools for efficient storage, analysis, and reporting.
- Analyzing Logs:
- Pay attention to failed logon attempts, privilege escalations, and unexpected changes in user rights.
- Use pattern recognition and anomaly detection to identify potential security breaches.
- Security Logs and Compliance:
- Security logs are key in demonstrating compliance with various regulations, such as HIPAA or GDPR, which require detailed auditing of access to sensitive data.
4. Using Windows Event Viewer for Auditing
Windows Event Viewer is an integral tool for viewing and analyzing the events recorded in security logs. It allows administrators to monitor security-relevant events and troubleshoot issues.
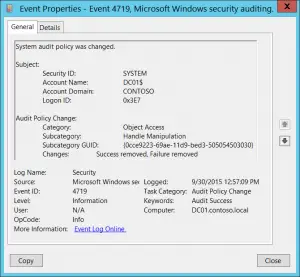
- Accessing Event Viewer:
- Open Event Viewer from the Control Panel or by running
eventvwr.msc. - Navigate to
Windows Logs→Securityto access security-related events.
- Open Event Viewer from the Control Panel or by running
- Custom Views for Efficient Monitoring:
- Create custom views to filter events based on criteria like event level, keywords, or specific event IDs.
- This tailors the Event Viewer to focus on events relevant to your security needs.
- Event Analysis:
- Understand the significance of different event IDs. For instance, ID 4625 indicates a failed logon attempt, which might signify a brute-force attack.
- Look for patterns or irregularities in the event logs that could indicate security issues.
- Integrating with Advanced Tools:
- For more complex environments, integrate Event Viewer with advanced monitoring tools or Security Information and Event Management (SIEM) systems for deeper analysis and real-time alerts.
By leveraging Windows Event Viewer effectively, administrators can gain valuable insights into their network security posture, enabling them to respond promptly to potential security threats.
5. Advanced Tools and Techniques for Windows Auditing
Beyond the built-in tools like Event Viewer, advanced tools and techniques can significantly enhance the effectiveness of Windows security auditing.
- Security Information and Event Management (SIEM) Systems:
- SIEM solutions like Splunk, LogRhythm, or IBM QRadar offer comprehensive monitoring by aggregating and analyzing data across the network.
- They provide real-time analysis, alerting, and advanced data correlation, essential for detecting complex threats.
- Intrusion Detection and Prevention Systems (IDPS):
- Tools like Snort or Microsoft’s Advanced Threat Analytics (ATA) can be integrated for enhanced monitoring of suspicious activities and potential intrusions.
- Automated Auditing Solutions:
- Automation in auditing helps in scheduling regular scans and reports, ensuring consistent monitoring.
- Tools like Nessus or ManageEngine ADAudit Plus automate vulnerability assessments and compliance checks.
- Custom Scripting and PowerShell:
- Develop custom scripts for specific auditing tasks. PowerShell scripts can automate the collection and analysis of log data, offering tailored insights.
- Data Analytics and Machine Learning:
- Leveraging data analytics and machine learning algorithms can help in predicting and identifying unusual patterns indicative of security breaches.
6. Best Practices in Windows Security Auditing
To maximize the effectiveness of Windows security auditing, adhere to these best practices:
- Regular Policy Review and Updates:
- Regularly review and update audit policies to align with evolving security needs and compliance requirements.
- Least Privilege Principle:
- Apply the least privilege principle to minimize the potential impact of compromised accounts.
- Comprehensive Log Monitoring:
- Monitor logs not just for failures, but also for unusual patterns of successful activities which could indicate covert breaches.
- Periodic Security Assessments:
- Conduct periodic security assessments and penetration tests to evaluate the effectiveness of your auditing strategies.
- Training and Awareness:
- Regularly train IT staff on the latest auditing tools and techniques. Promote security awareness across all organizational levels.
- Disaster Recovery Planning:
- Ensure that your auditing strategy includes provisions for backup and recovery in the event of data loss or network failure.
By implementing these advanced tools and adhering to best practices, organizations can significantly enhance the security and integrity of their Windows-based networks.
7. Case Studies: Real-World Applications
- Financial Institution Enhances Security with Windows Auditing:
- A large bank implemented comprehensive Windows auditing to monitor and secure its network.
- Focused on tracking privileged user activities and ensuring compliance with financial regulations.
- Resulted in early detection of unauthorized access attempts and reinforced overall data security.
- Healthcare Provider Meets Compliance Standards:
- A healthcare organization used Windows security logs to safeguard patient data.
- Emphasized auditing access to sensitive health records, aligning with HIPAA requirements.
- Achieved a robust compliance posture and enhanced patient data protection.
- Educational Institution Prevents Data Breaches:
- A university deployed advanced auditing tools within its Windows network to monitor user activities.
- Detected and thwarted a malware attack through analysis of irregular logon patterns.
- Strengthened defense mechanisms against future cybersecurity threats.
8. Conclusion
Navigating the complexities of network security auditing in Windows environments is a formidable yet essential task for maintaining a secure and compliant network. From setting up audit policies to utilizing tools like Event Viewer, this article has explored various facets of Windows security auditing.
The real-world case studies underline the practical applications and benefits of effective auditing strategies. As cyber threats evolve, staying informed and proactive in security auditing will continue to be crucial for organizations across all sectors.
9. References
- Books:
- “Windows Security Monitoring: Scenarios and Patterns” by Andrei Miroshnikov
- “Microsoft Windows Security Essentials” by Darril Gibson
- RFCs: