The Application Layer, positioned as the topmost layer in the Open Systems Interconnection (OSI) model, is pivotal in network architecture. It serves as the window for users and applications to access network services.
This article delves into the nuances of the Application Layer, exploring its functions, protocols, and significance in enabling network communication and application services. It’s an essential read for anyone looking to deepen their understanding of network protocols and how they facilitate effective communication in digital networks. Let’s begin!
Table of Contents:
- Overview of the Application Layer
- Protocols in the Application Layer
- Real-World Applications of the Application Layer
- Interaction with Other OSI Layers
- Challenges and Solutions in the Application Layer
- Conclusion
- References
1. Overview of the Application Layer
Role and Function
Interface to Network Services:
The Application Layer in the OSI model is the conduit through which end-users and applications communicate with network services. This layer is the user’s gateway to the network, where application-level communications like email sending, file transfers, and website access occur. It encapsulates user-level processes and facilitates the interpretation of requests and responses between the network and the user.
- Responsibility for Service Requests and Responses: The Application Layer is accountable for initiating service requests to other network devices and handling incoming responses. It translates user actions and commands into network operations, ensuring that the requests are understandable and executable by the lower layers of the OSI model.
Data Exchange Formats:
One of the critical functions of the Application Layer is to define the standards and structures for data exchange formats.
- Protocol Definitions for Syntax and Encryption: This layer specifies protocol rules, including syntax, semantics, and synchronization of communication. Protocols like HTTP for web browsing and SMTP for email rely on the Application Layer for these specifications.
- Session Management: It is responsible for managing sessions, ensuring that data transfers are complete and accurate. This management includes maintaining data integrity and security during communication.
Key Responsibilities
Resource Sharing:
The Application Layer plays a vital role in enabling the sharing of resources over a network.
- Efficient Utilization of Network Resources: It allows multiple users to access and utilize shared network resources such as printers and files, optimizing resource use and improving collaboration efficiency.
Remote File Access:
This layer facilitates access to files located on remote servers, making it a cornerstone for distributed computing and cloud storage services.
- Access and Management of Files Over a Network: Users can retrieve, modify, and store files on a server located remotely, enhancing accessibility and data mobility.
Mail Services:
One of the most commonly used services of the Application Layer is in the domain of email communication.
- Management of Email Transmission and Storage: Protocols like SMTP (Simple Mail Transfer Protocol) and POP3 (Post Office Protocol 3) operate at this layer to manage the sending, receiving, and storing of emails. This functionality includes directing emails to the correct recipients and storing them appropriately for later retrieval.
2. Protocols in the Application Layer
The Application Layer of the OSI model hosts a variety of protocols, each designed to fulfill specific communication and data transfer needs across the network. These protocols define how data is formatted, transmitted, and received, and they often incorporate security measures to safeguard data integrity and confidentiality.
Common Protocols
HTTP (Hypertext Transfer Protocol):
HTTP stands as the foundational protocol for data communication on the World Wide Web. It facilitates the transfer of hypertext and multimedia content over the internet.
- Function: HTTP defines how messages are formatted and transmitted, and how web servers and browsers should respond to various commands.
- Use Case: When a user visits a website, their browser sends an HTTP request to the server hosting the site, which then responds with the requested pages.
SMTP (Simple Mail Transfer Protocol):
SMTP is the standard protocol for sending emails across the internet.
- Function: It governs the sending of emails from a client to a mail server and from server to server.
- Use Case: When an email is sent, SMTP routes it from the sender’s email server to the recipient’s email server.
FTP (File Transfer Protocol):
FTP is used for the transfer of files between a client and a server on a network.
- Function: It provides a way for users to upload, download, and manage files on a remote server.
- Use Case: FTP is often used for transferring large files, managing website files, or for backup systems.
DNS (Domain Name System):
DNS translates human-readable domain names (like www.example.com) into machine-readable IP addresses.
- Function: It ensures users can access websites using familiar domain names instead of having to remember numerical IP addresses.
- Use Case: When a user types a URL into their browser, DNS servers translate it into an IP address that points to the web server hosting that site.
Protocol Characteristics
Communication Standards:
Each protocol in the Application Layer has a set of specific rules and standards governing communication.
- Data Formatting and Encapsulation: Protocols define the structure of the messages exchanged, including headers, footers, and payload organization.
- Data Delivery Mechanisms: They specify how data should be transmitted, ensuring compatibility and interoperability between different systems and devices.
Security Measures:
Many Application Layer protocols include built-in security features to protect data integrity and confidentiality.
- Encryption: Protocols like HTTPS (an extension of HTTP) incorporate encryption to secure data transmission, especially important for sensitive transactions.
- Authentication: Protocols often have mechanisms for verifying the identity of users and devices, ensuring that only authorized entities can access data or services. For example, email protocols have authentication methods to verify users before allowing access to email accounts.
3. Real-World Applications of the Application Layer
The Application Layer in the OSI model is integral to numerous everyday and advanced technological functionalities. This chapter explores the real-world applications of the Application Layer, demonstrating its ubiquity and critical role in modern computing and communication.
Everyday Use Cases
Web Browsing:
One of the most common uses of the Application Layer is in web browsing, where HTTP and HTTPS protocols are fundamental.
- HTTP and HTTPS: These protocols are used for accessing and transmitting web content. While HTTP facilitates the basic exchange of information over the web, HTTPS adds a layer of security through encryption, ensuring safe data transfer, especially for sensitive transactions like online banking or shopping.
- Use Case Example: Accessing any website through a browser involves sending an HTTP request, which is handled by the Application Layer.
Email Communication:
Email communication relies heavily on protocols operating at the Application Layer, such as SMTP, POP3, and IMAP.
- SMTP: Used primarily for sending emails.
- POP3 and IMAP: Used for retrieving emails from a server. While POP3 downloads emails to the local device, IMAP allows users to view emails directly from the server, facilitating access from multiple devices.
- Use Case Example: Sending an email through an email client uses SMTP, while checking for new emails utilizes POP3 or IMAP.
File Transfers:
Protocols like FTP and SFTP provide mechanisms for file uploads and downloads, essential in numerous contexts.
- FTP and SFTP: FTP is used for transferring files between computers on a network, while SFTP adds a layer of security by encrypting data transfers.
- Use Case Example: Uploading files to a web server for website maintenance or downloading large data files from a remote server.
Advanced Implementations
APIs and Web Services:
Application Layer protocols are pivotal in the functioning of APIs and web services, which are fundamental to modern web applications and services.
- Role in APIs: These protocols enable different software applications to communicate and exchange data, whether they are on the same network or across the internet.
- Web Services: RESTful web services commonly use HTTP/HTTPS for operations, allowing for interoperable machine-to-machine interaction.
- Use Case Example: A mobile app retrieving weather data from a remote server using a web service.
Cloud Computing:
In cloud computing, Application Layer protocols are instrumental in delivering various services, including Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
- SaaS: Protocols enable users to access software applications over the internet.
- PaaS and IaaS: They facilitate the delivery of computing platforms and infrastructure as services over the internet, allowing developers and users to access and utilize cloud-based resources.
- Use Case Example: Accessing a cloud-based CRM system (SaaS) or deploying applications on cloud platforms (PaaS).
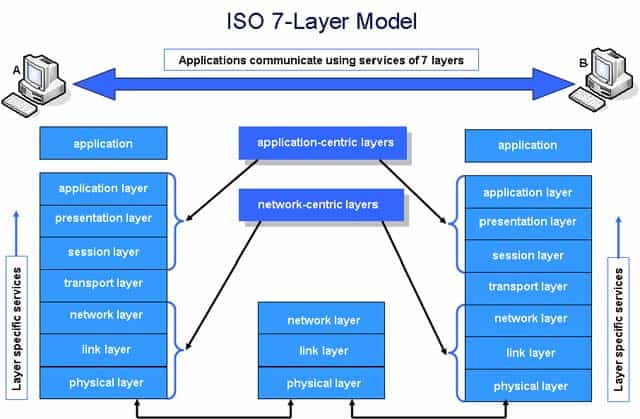
4. Interaction with Other OSI Layers
In the OSI model, the Application Layer does not operate in isolation; it interacts synergistically with the Presentation and Session layers to facilitate complete and efficient communication processes.
Session and Presentation Layers
Data Preparation:
The Application Layer closely works with the Presentation Layer, which is responsible for data format translation. This translation includes converting data from a format used by the application layer into a common format at the sending station and then back into the application’s format at the receiving station.
- Role of the Presentation Layer: It handles the syntax and semantics of the information transmitted, ensuring that data from the application layer of one system is understandable by the application layer of another system.
- Example: Converting different file formats (JPEG, PDF, etc.) into a standard format for transmission and then back into their original formats upon receipt.
Session Management:
The Application Layer also collaborates with the Session Layer to manage and control the dialogue between computers. It establishes, manages, and terminates the connections between the local and remote application.
- Control of Dialogues: The Session Layer sets up, coordinates, and terminates conversations, exchanges, and dialogues between the applications at each end. It deals with session and connection coordination.
- Example: Managing a continuous file transfer operation, ensuring data synchronization and orderly communication.
5. Challenges and Solutions in the Application Layer
Security Concerns
Vulnerability to Attacks:
The Application Layer is frequently targeted in cyber attacks, such as data breaches and DDoS attacks. These attacks can exploit vulnerabilities in application layer protocols to gain unauthorized access or disrupt services.
- Mitigation Strategies: Implementing firewalls and intrusion detection/prevention systems to monitor and filter malicious traffic. Regularly updating and patching applications to fix security vulnerabilities.
- Example: Deploying web application firewalls to protect web applications from various attacks.
Encryption and Authentication:
To protect data integrity and confidentiality, robust encryption and authentication mechanisms are critical in the Application Layer.
- Implementing Encryption: Using protocols like HTTPS, which incorporates SSL/TLS encryption, to secure data transmissions.
- Strong Authentication Protocols: Implementing authentication methods like OAuth and two-factor authentication to verify user identities and prevent unauthorized access.
- Example: Secure online transactions using HTTPS, ensuring data like credit card details are encrypted and secure.
Performance Optimization
Load Balancing:
Load balancing is essential for managing high network traffic, ensuring that no single server bears too much demand.
- Techniques: Distributing workload evenly across multiple servers to maximize throughput, minimize response time, and avoid overloading any single server.
- Example: Using DNS round-robin technique to distribute incoming requests evenly across multiple servers.
Protocol Efficiency:
Optimizing protocols at the Application Layer can greatly improve performance and reduce latency.
- Streamlining Protocols: Ensuring protocols are as efficient as possible, reducing overhead, and improving speed.
- Data Compression: Implementing data compression techniques to reduce the amount of data being transmitted, thereby increasing speed and efficiency.
- Example: Minimizing HTTP requests in web applications to improve page load times.
In summary, the Application Layer’s interaction with other layers in the OSI model enhances its functionality, particularly in data preparation and session management. However, it faces challenges in terms of security and performance, which can be addressed through robust security protocols, efficient load balancing, and protocol optimization. These measures are crucial for maintaining the integrity, security, and efficiency of Application Layer operations.
6. Conclusion
The Application Layer in the OSI Model is a cornerstone in network communication, playing a crucial role in facilitating user interactions and data exchange over networks.
Its protocols and services form the basis of many of our daily digital interactions, from web browsing to file sharing. Understanding the intricacies of this layer is fundamental for network professionals, developers, and anyone interested in the mechanics of network communication.
7. References
- “Computer Networking: A Top-Down Approach” by James Kurose and Keith Ross
- “Data Communications and Networking” by Behrouz A. Forouzan
- Online Resources:
- IETF Protocol Specifications
- OSI Model Overview by the International Organization for Standardization