Category: Cryptography
-

Quantum Threat: Can Quantum Computers Break Bitcoin?
Explore how quantum computing could disrupt Bitcoin by breaking SHA-256 and cracking private keys, and what can be done to prevent this.
-

Transport Layer Security (TLS): Beyond the Basics
Unlock the secrets of Transport Layer Security (TLS) to ensure optimal data security. This comprehensive guide explores TLS protocols, encryption, myths, and more.
-

Why Encrypted Passwords Are Non-Negotiable
Discover why encrypted passwords are crucial for safeguarding data. Learn about encryption methods, vulnerabilities, and best practices in this comprehensive guide.
-
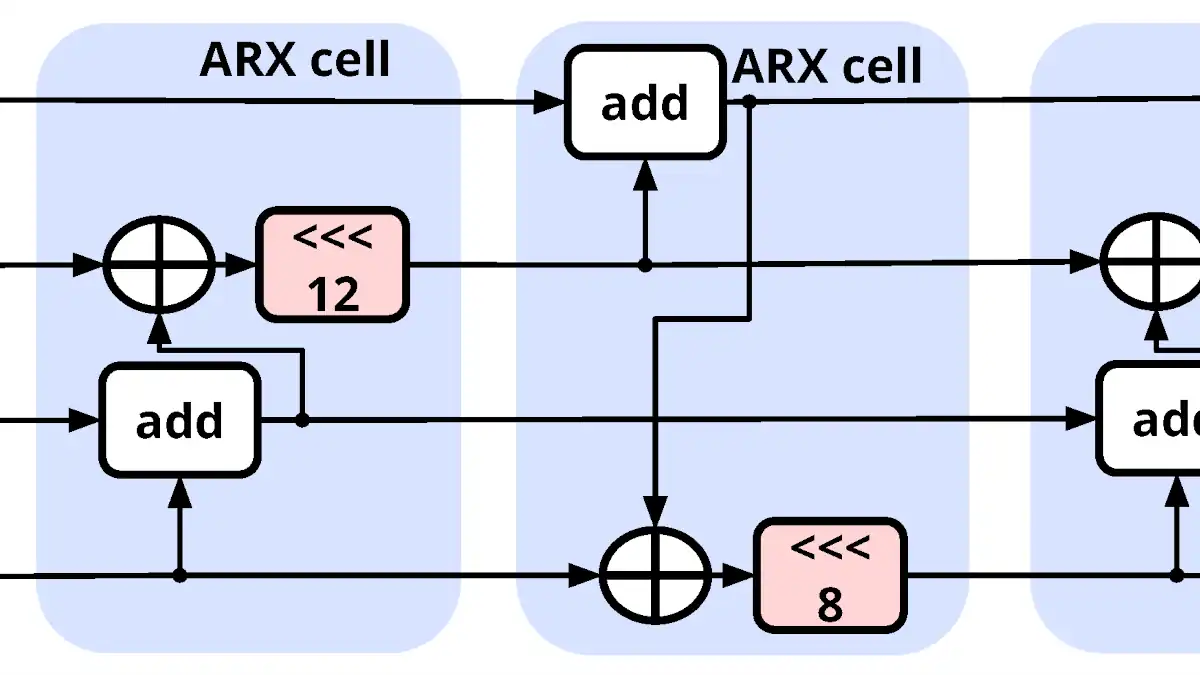
ChaCha20: The Dance of Cryptography
Dive deep into ChaCha20’s intricate dance of encryption. Explore the mathematics and design that make this cryptographic algorithm both potent and elegant.
-
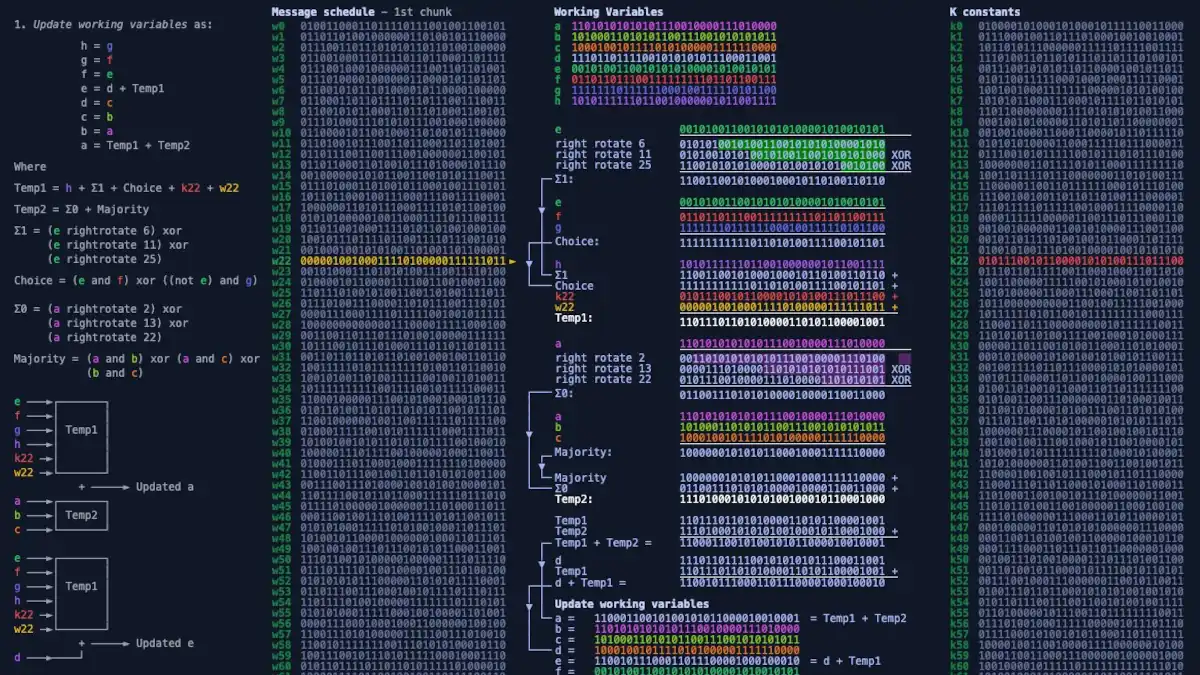
SHA-256 Unmasked: Deciphering Cryptographic Hash Functions
Unveil the world of cryptographic hash functions as we break down SHA-256. Understand its vital role in ensuring data integrity and security in the digital realm.
-

Asymmetric Encryption
Asymmetric encryption requires the use of two keys: a private key that is known only by its owner and a public key that is readily available to those who need to use it.
-
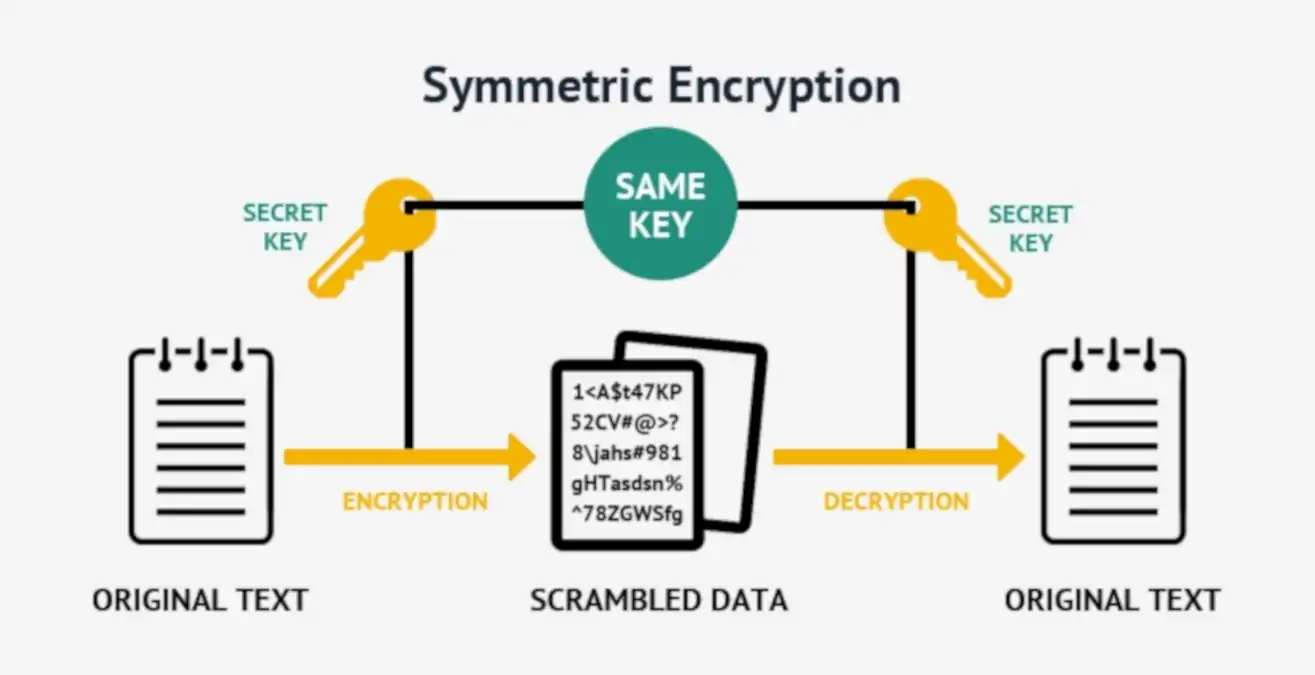
Symmetric Encryption
Symmetric encryption, or single-key encryption, is the most well-understood cryptography primitive.
-

Starting to understand Encryption
Encryption is the principal application of cryptography; it makes data incomprehensible in order to ensure its confidentiality.
-

CryptoAPI
CryptoAPI is a core component of the latest versions of Microsoft Windows that provides application programming interfaces (APIs) for cryptographic security services that provide secure channels and code signing for communication between applications.
-

Secure Hypertext Transfer Protocol (S-HTTP)
Unveil the essentials of S-HTTP, the protocol for encrypting HTTP traffic. Explore its creation, functionality, current usage, and comparison with HTTPS.
