Category: Letter B
-
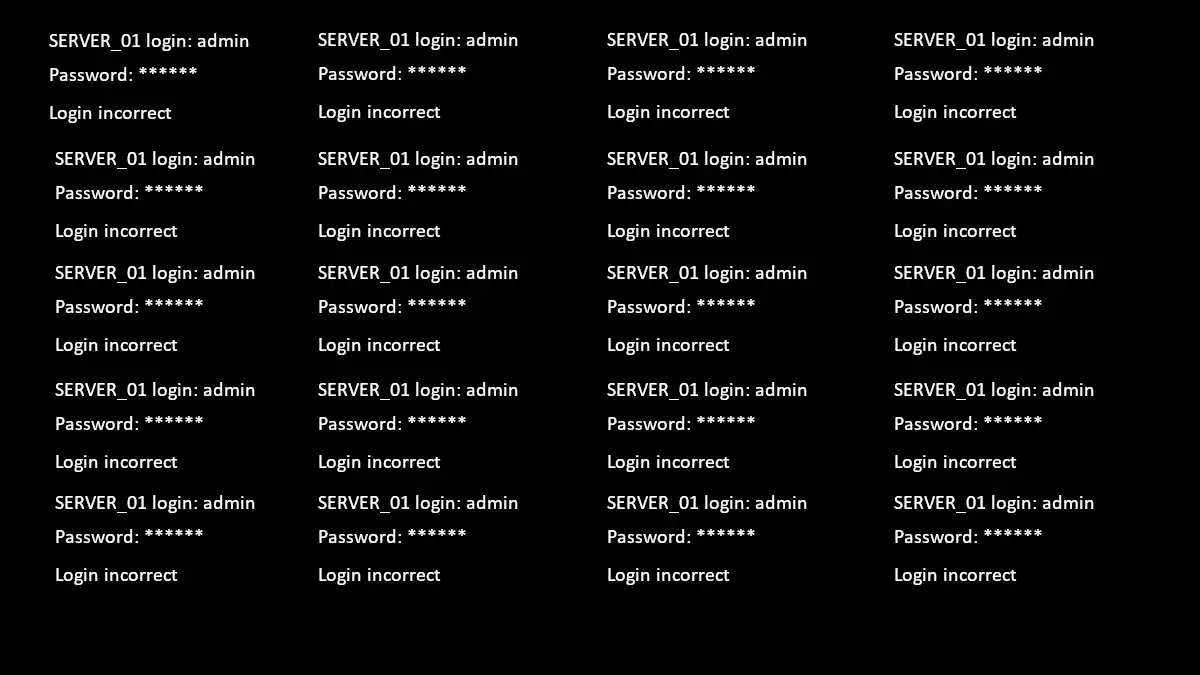
Brute-Force Attack
Learn what a brute-force attack is, real-world examples, and foolproof strategies to protect yourself. Your ultimate guide to understanding and combating this pervasive cyber threat.
-

Blockchain Technology: Revolutionizing Trust and Transactions
Unlock the future with blockchain technology—a secure, transparent, and decentralized way of recording transactions. Dive in to understand its mechanisms, benefits, and global impact.
-
Botnet Herding: Mastering the Art of Cyber Control
Explore the intricate world of Botnet Herding: how hackers build, control, and deploy botnets for cyberattacks. Become aware to stay secure.
-
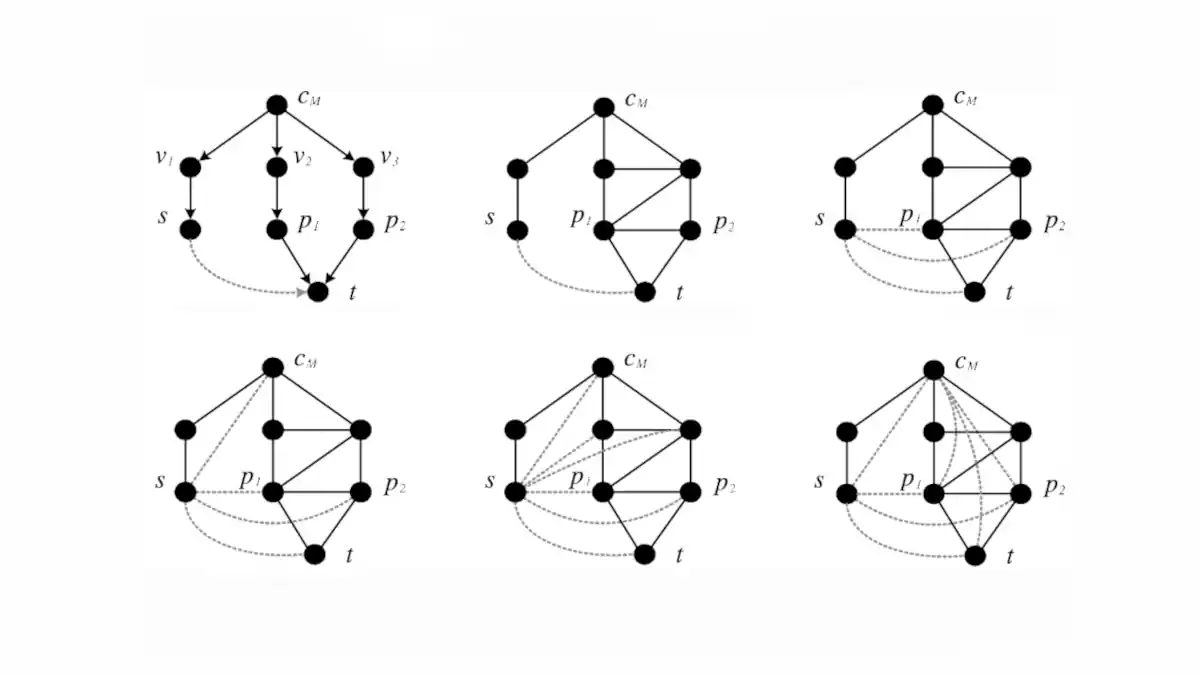
Bayesian Network: Deciphering its Intricacies
Dive deep into Bayesian Networks—a cornerstone of modern AI, merging statistics and graph theory to model complex systems
-
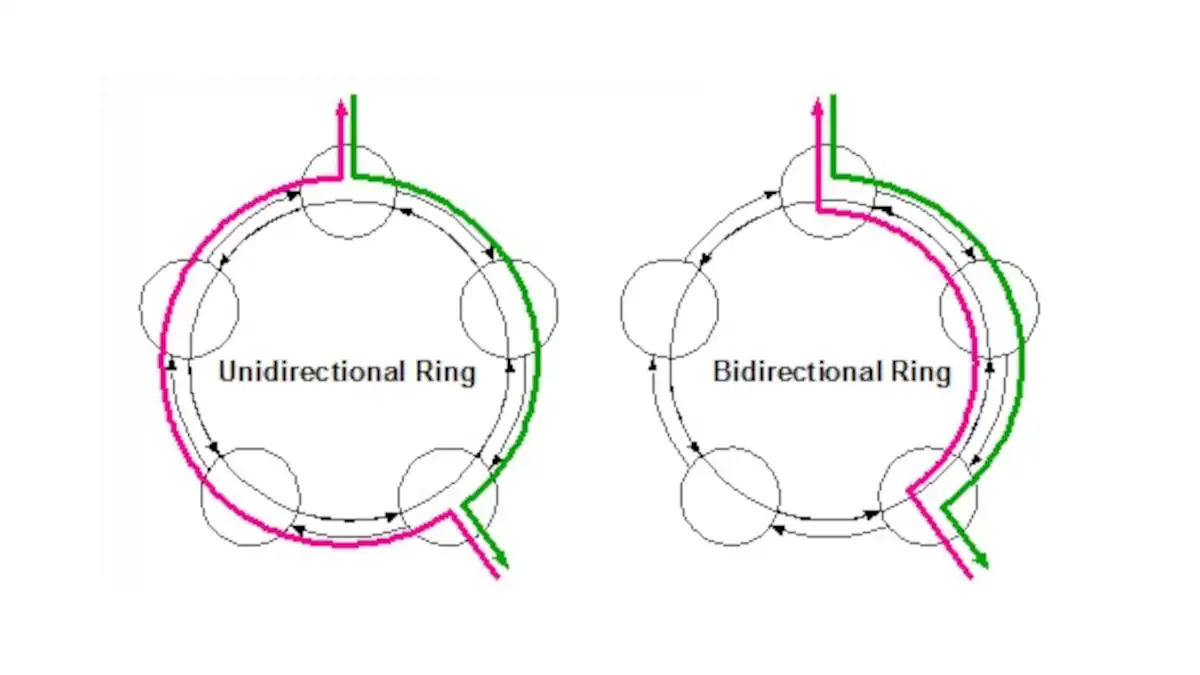
Bidirectional Path Switched Ring (BPSR)
A bidirectional path switched ring (BPSR) is a type of network architecture that uses a ring topology to transmit data between nodes.
-
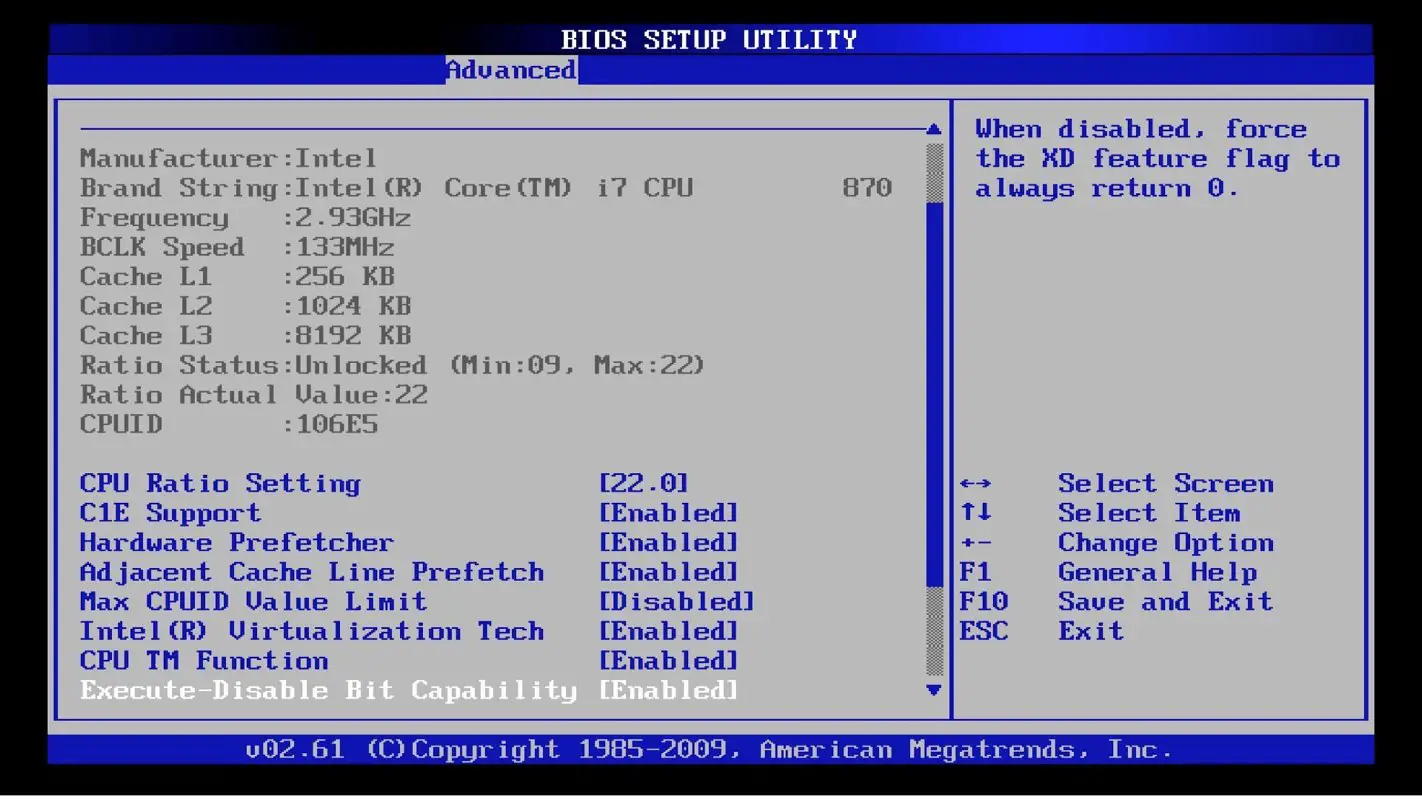
BIOS – Basic Input/Output System
BIOS is one key component of the computer motherboard. It stands for basic input/output system (BIOS).
-

Entering the Brave (Browser) New World!
Brave browser arrived to change the way we surf the internet. In this article, we will explain what Brave browser is and how you can benefit from it.
-
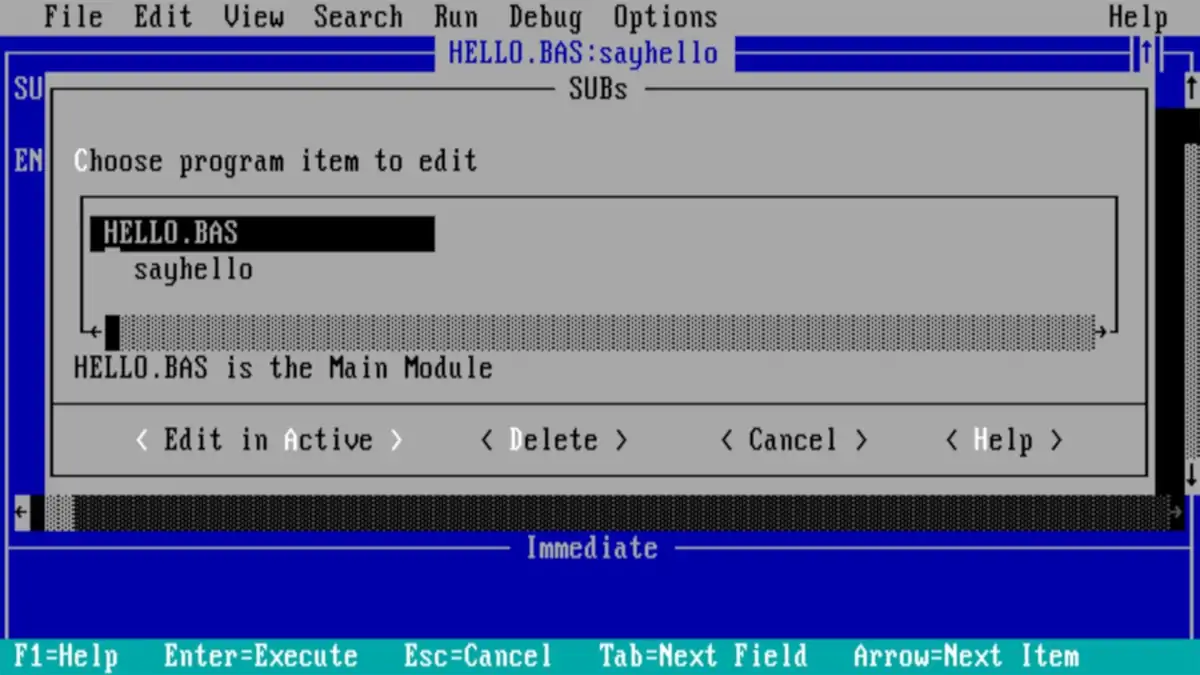
BASIC Programming Language
The BASIC Programming Language was originally developed at Dartmouth College in 1964. BASIC stands for Beginners’ All-purpose Symbolic Instruction Code.
-
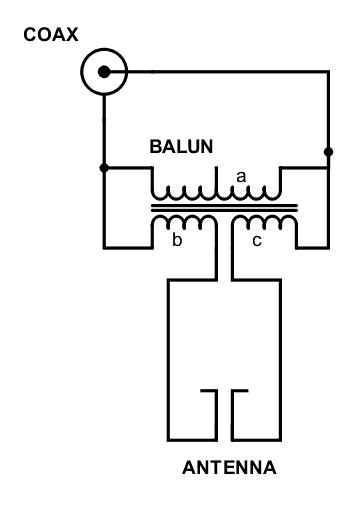
Balun
Unlock the complexities of Balun in networking. Learn its importance, types, and applications to improve network performance and reliability.
-
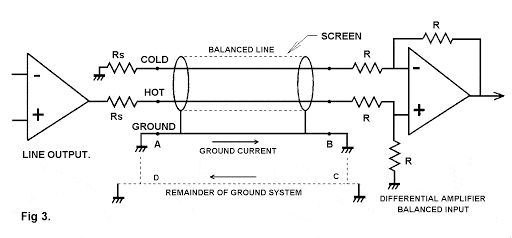
Balanced Line
Explore the world of Balanced Lines, their importance in network cabling, and how they enhance signal integrity in data transmission.

