In the vast cosmos of computer network architectures, the OSI (Open Systems Interconnection) Model stands as a paramount framework, a beacon illuminating the complexities of network communication. This seven-layered conceptual model, akin to the fabled seven-layered rainbow, paints a vivid picture of how data is packaged, transported, and processed from one network node to another. Ascending this technicolor arch, we arrive at the summit – the 7th Layer, or the Application Layer, the epitome of user interaction with the network.
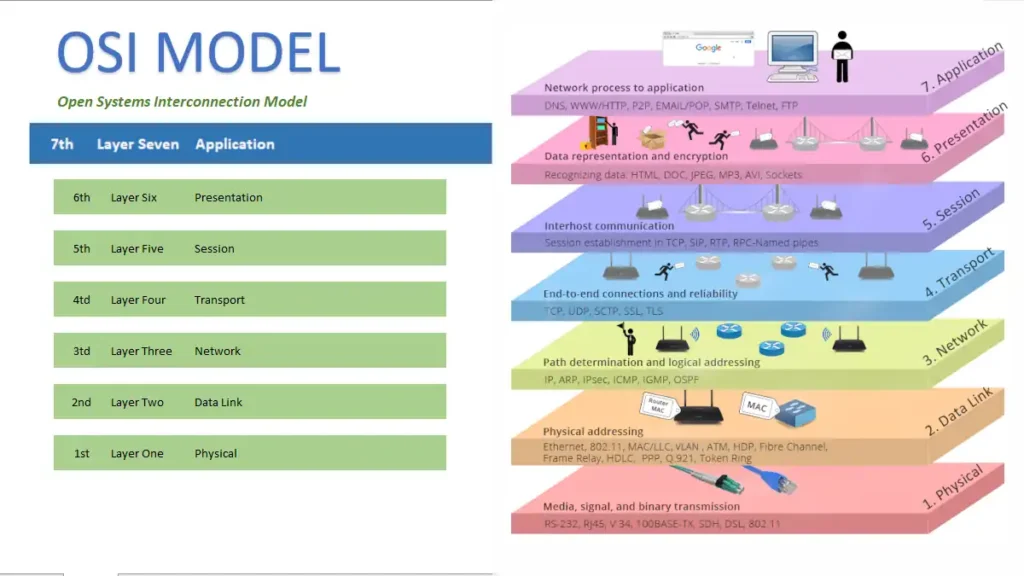
The Application Layer, often underestimated in its prominence, acts as the interface between the network and the user’s applications. It breathes life into the skeletal structure of network architecture, transforming it into a dynamic entity that directly interacts with the user’s data and software. This layer’s nuances and operations, often obscured by its seeming simplicity, are key to fully grasping the OSI Model’s structure and functioning.
Peeling the 7th Layer of the OSI Model
In the realm of network communication, the Application Layer is the maestro, orchestrating the symphony of data exchange between the user and the network. Being the topmost layer of the OSI Model, it serves as the gateway for networking applications to access network services. It handles high-level protocols, including HTTP (HyperText Transfer Protocol), SMTP (Simple Mail Transfer Protocol), FTP (File Transfer Protocol), and DNS (Domain Name System), among others.
However, the Application Layer is more than just a doorman. It provides a suite of functionalities that facilitate seamless interaction between the user and the network. It manages network connections, controls the flow of data, ensures complete and correct data transfer, and provides services for email, file transfer, and web browsing. Essentially, it is this layer that makes the network usable and accessible for applications and end-users.
Understanding the Application Layer’s workings is like unpeeling an onion. Each peel represents a different function or protocol, and understanding each layer provides a more comprehensive view of the Application Layer’s role in network communication. This understanding paves the way for efficient network design, effective problem-solving, and successful network operation.
The Functionality Matrix: Unfurling the Capacities of the Application Layer
Within the layered orchestra of the OSI Model, the Application Layer, as the conductor, wields the baton with great finesse, coordinating an intricate ballet of functionalities that permit the smooth flow of data from user-end applications to the network, and vice versa. Each note it strikes, each rhythm it guides, translates into a specific function, all of which converge to create a harmonious user experience in the realm of network communication.
Network Transparency
One of the most significant attributes of the Application Layer is its capacity to render network operations transparent. As the closest layer to the user, it masks the underlying complexities of the network processes. From a user’s perspective, data seamlessly slides into the network and arrives intact at the destination, without any insight into the labyrinth of processes it undertakes in between. This simplicity, this illusion of ease, is a direct result of the Application Layer’s ability to veil the operations of the network, thus enhancing the user experience.
Session Management
The Application Layer also serves as the handshake initiator and terminator. It handles the opening, maintaining, and closing of sessions between end-user application processes. This includes aspects like login and logout procedures, and ensuring that a secure and managed connection is established and terminated between the user’s application and the network.
Data Syntax Transformation
In the realm of data exchange, the Application Layer takes on the mantle of a translator. Data from the application is often in a format that the network may not recognize or handle. The Application Layer transforms this application-specific format into a syntax that is network-compatible. This translation process ensures that data can smoothly navigate the network without encountering any format-related hitches.
Control of Data Transfer
As the maestro of the data symphony, the Application Layer directs the flow and rhythm of data transfer. It controls whether the data transfer between applications will occur in simplex (one-way), half-duplex (two-way, but not simultaneously), or full-duplex (two-way and simultaneous) mode. It also manages the pace of data flow, dictating whether the data transfer will be synchronous (fixed pace) or asynchronous (variable pace).
Service Advertisement and Discovery
One lesser-known, but equally crucial, function of the Application Layer is the advertisement of network services. Applications need to know what network services are available, and the Application Layer facilitates this discovery. On the flip side, it also allows network services to advertise their capabilities to the applications, creating an efficient two-way communication channel.
Error Handling
The Application Layer is also the first line of defense when it comes to error handling. It checks for errors at the application level and tries to recover lost packets if any. In case of irrecoverable errors, it alerts the user or the application about the issue, allowing for prompt troubleshooting.
Through this prism of functionalities, the Application Layer rises as a pivotal player in the network communications symphony, one that makes the chaotic dance of data transmission appear as a seamless, harmonious ballet to the end-user.
Real-world Use Cases: The Application Layer in Action
Navigating through the nuanced terrain of theory and technical definitions often leaves us yearning for tangible anchors, relatable instances where these concepts come to life. Let’s walk through a few real-world scenarios where the Application Layer of the OSI Model takes center stage, painting vivid portraits of this key player in the network symphony.
1. Surfing the World Wide Web
Imagine embarking on a digital voyage through the vast seas of the internet, a journey as commonplace as our daily cup of coffee. The web browser, our trusty ship, employs the Hypertext Transfer Protocol (HTTP), a protocol of the Application Layer. As we type in a URL, the Application Layer gets to work. It engages HTTP to request the web page from the server, then receives the web page data and forwards it to our browser, making the webpage magically appear on our screen.
2. Emailing across Continents
Picture drafting an email, attaching a report, and clicking send. In the blink of an eye, your message wings its way across continents to land in your colleague’s inbox. The Application Layer is the unseen hero here, leveraging the Simple Mail Transfer Protocol (SMTP) to handle the email’s transfer across networks. It ensures your message is correctly formatted, delivered, and accessible to your colleague.
3. Downloading Files
Consider the action of downloading a file from a website or a cloud repository. The act of transferring a file from a server onto your local machine involves the File Transfer Protocol (FTP), yet another resident of the Application Layer. FTP manages the smooth transfer of files over the network, ensuring the data arrives intact and without corruption.
4. Online Gaming
Dive into the exhilarating realm of multiplayer online gaming, where players across the globe unite in shared virtual playgrounds. Real-time data transfer, synchronization, and low latency are critical here. The Application Layer flexes its prowess, managing these data exchanges via specific gaming protocols and interfaces.
5. Streaming a Movie
When you sit back to enjoy a movie on your favorite streaming platform, the Application Layer is at work, facilitating the streaming data’s flow. Using Real-time Streaming Protocol (RTSP), ensures a seamless, buffer-free movie experience, orchestrating the delicate ballet of data packets that constitute your movie stream.
6. Domain Name System
Every time you use a human-friendly domain name like ‘www.example.com’ instead of a machine-friendly IP address, you’re employing the Domain Name System (DNS) protocol of the Application Layer. DNS translates these domain names into their corresponding IP addresses, a crucial task for data routing in networks.
Through these use cases, the Application Layer’s importance, flexibility, and prowess become unmistakably clear. It is the silent orchestrator, making our everyday digital interactions smooth and intuitive. The abstract concepts associated with the Application Layer take on a concrete, relatable form, bridging the gap between theory and practice, between lines of code and lines of communication.
Conclusion: Decoding the Digital Maestro
As we conclude our deep dive into the multifaceted world of the 7th layer of the OSI Model – the Application Layer – we emerge with a newfound appreciation for the invisible strings that orchestrate our daily digital symphony. The Application Layer is not just a technical construct; it is the unseen maestro that dictates the rhythm and melody of our network interactions.
From browsing webpages to sending emails, from downloading files to streaming movies, from multiplayer gaming to handling domain names, the Application Layer operates subtly yet significantly in the backdrop of every digital activity we undertake. It is the bridge between users and the network, the gatekeeper of data, and the translator of protocols.
The Application Layer, in its complexity and capability, showcases the artistry hidden within the science of networking. It transforms the binary, the code, the protocols into a seamless, user-friendly experience. As future engineers and architects of digital landscapes, understanding and appreciating this layer equips us to design, troubleshoot, and optimize networks with increased acumen and proficiency.
Thus, we conclude our exploration of the Application Layer, but let this not be an end. Instead, let it be a launching pad for further investigation, a springboard for deeper curiosity, and a stepping stone towards mastering the intricate, fascinating world of computer networks. Here’s to a future where we don’t just use networks; we shape them!