Category: Network Security
-

Phishing Exposed: Understanding Digital Deception
Delve deep into the dark world of Phishing, as we unravel the mechanics of this notorious cyber menace, empowering you to navigate the digital realm securely
-
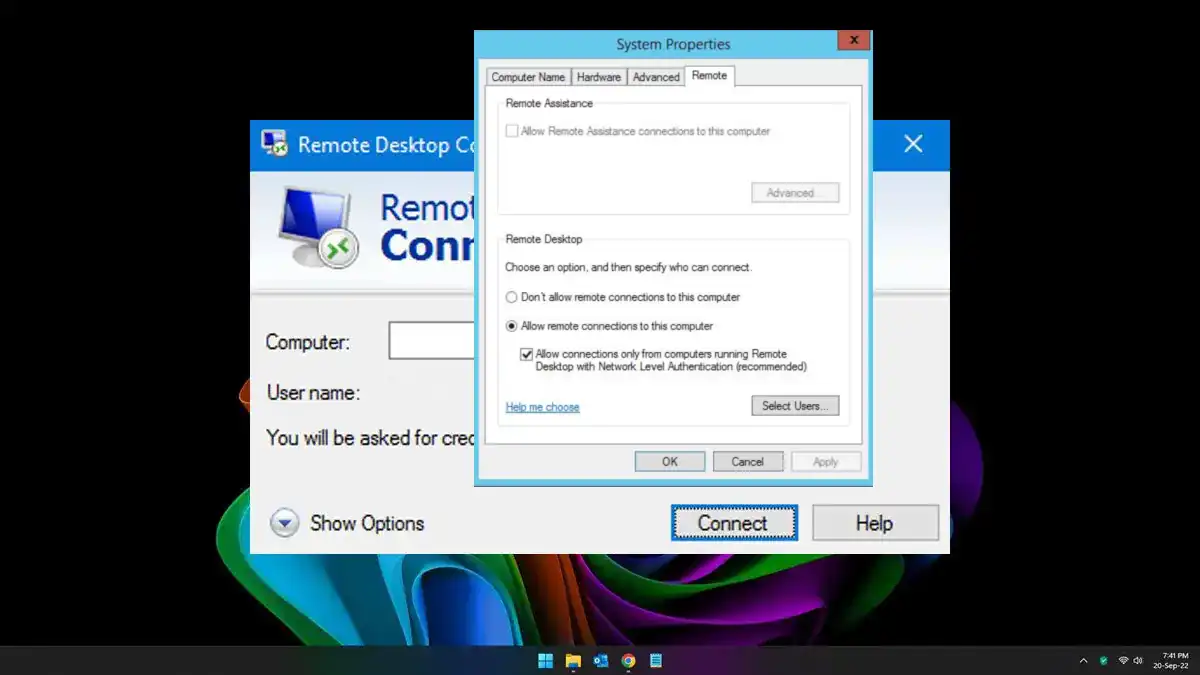
Network Level Authentication (NLA): Securing Connections
Don’t miss this beginner-friendly guide to understanding the mechanism of Network Level Authentication (NLA).
-
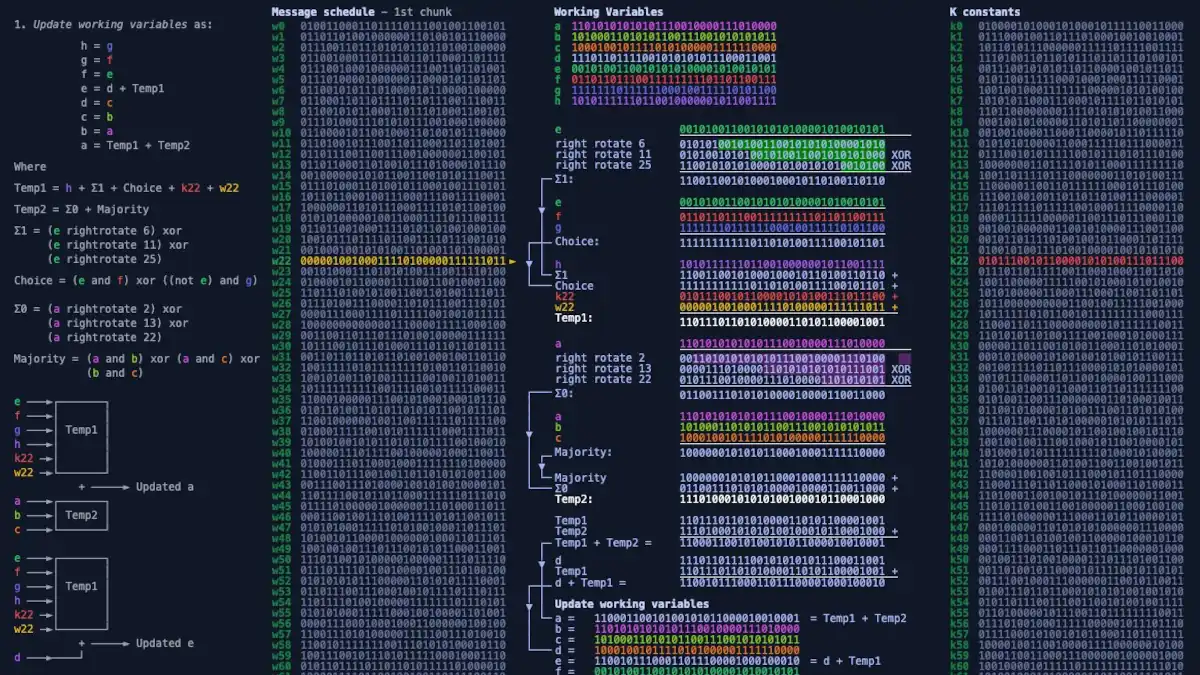
SHA-256 Unmasked: Deciphering Cryptographic Hash Functions
Unveil the world of cryptographic hash functions as we break down SHA-256. Understand its vital role in ensuring data integrity and security in the digital realm.
-

Difference between port 80 and port 443
Port 80 and port 443 are both used for transmitting HTTP and HTTPS traffic, respectively, but they operate at different layers of the networking stack and use different protocols.
-
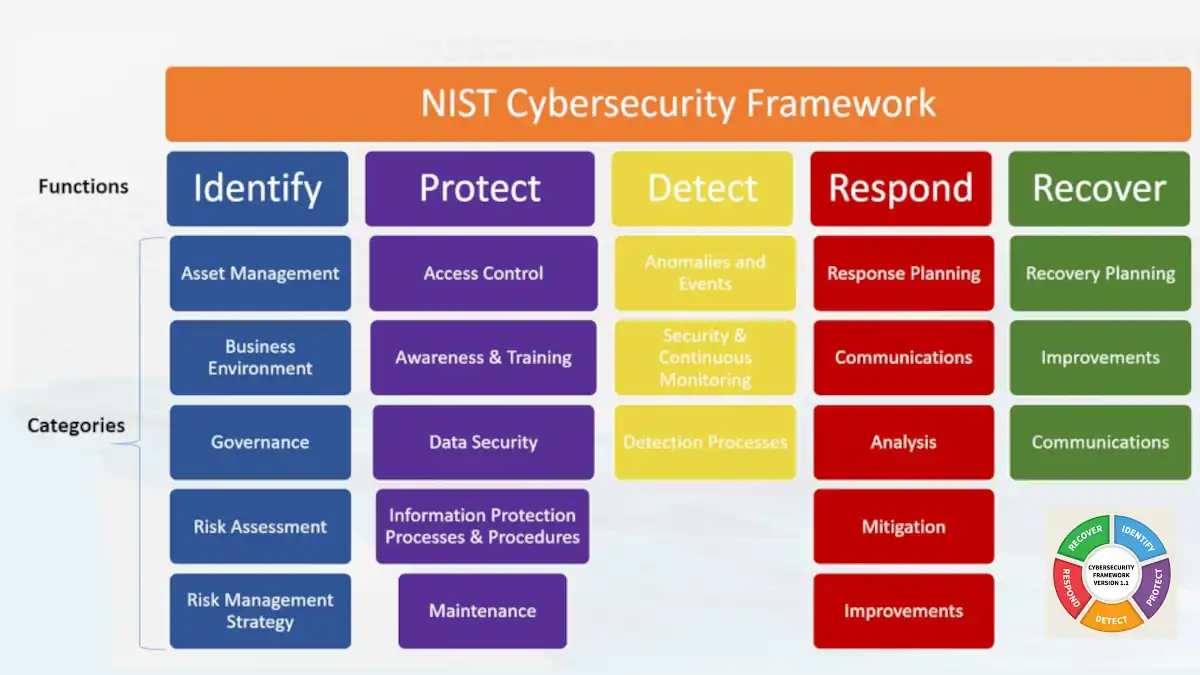
National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a set of guidelines and best practices for managing cybersecurity risks in an organization.
-
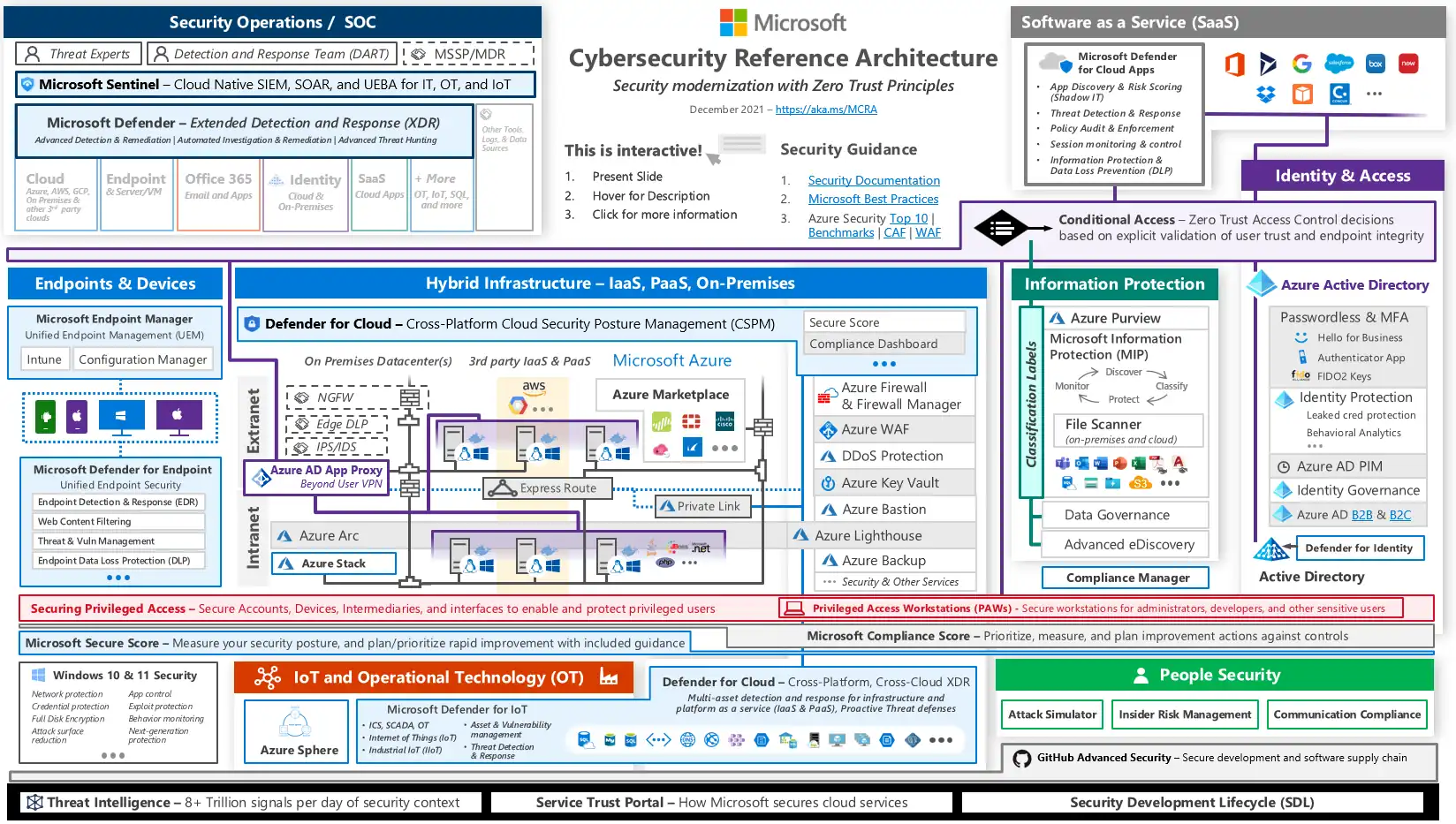
Microsoft Cybersecurity Reference Architectures (MCRA)
Microsoft Cybersecurity Reference Architectures (MCRA) is a set of documents and resources provided by Microsoft that outline recommended approaches for designing and implementing secure systems and networks.
-

Edge Traversal
Edge Traversal refers to the ability of a packet to pass from one network to another network at the edge or boundary of the first network.
-

Common Security Threats in Computer Networks
In this article, we will explain the most common security threats in computer networks. This allows you to be aware of those threats.
-

Asymmetric Encryption
Asymmetric encryption requires the use of two keys: a private key that is known only by its owner and a public key that is readily available to those who need to use it.
-
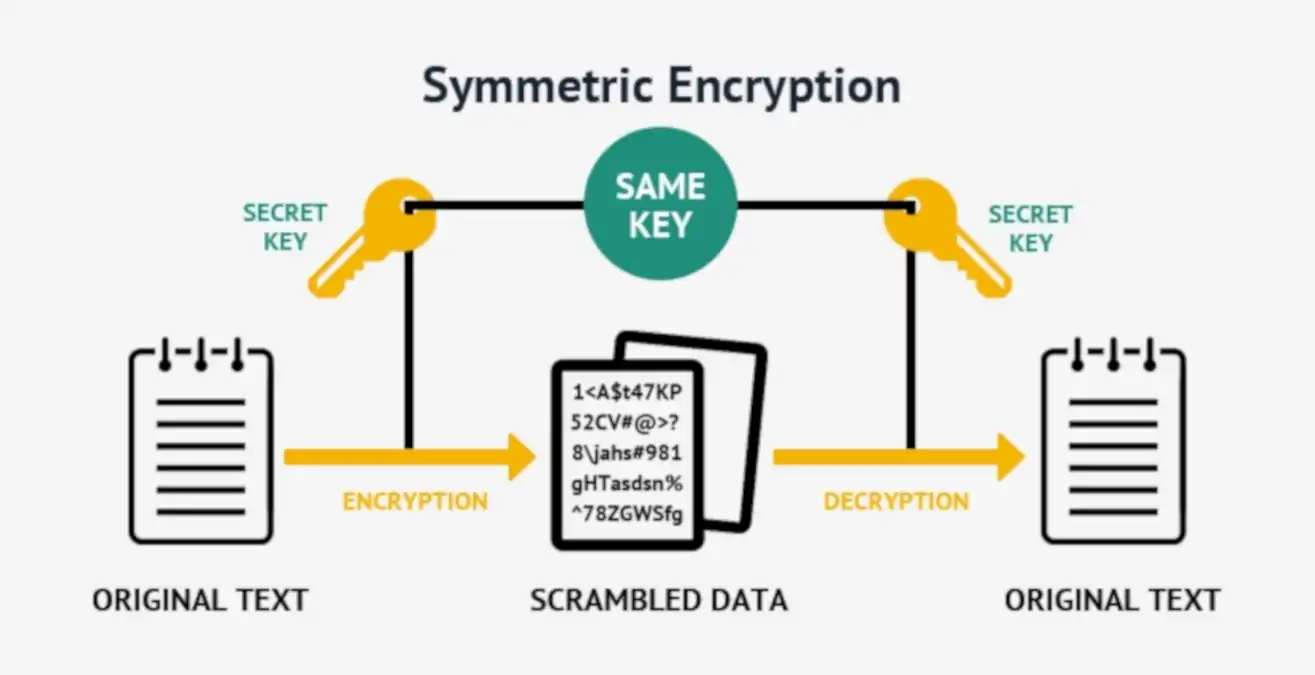
Symmetric Encryption
Symmetric encryption, or single-key encryption, is the most well-understood cryptography primitive.
-

Importance of Cyber Security in the Digital Era
Cyber Security in the Digital Era: It is crucial to understand what we are exposed to online and how to protect ourselves from potential attacks.
-
Credentials
Unlock the layered world of credentials in computer science and networking. Learn the types, uses, and best practices. Your key to understanding security.